New
#1
port 53 I have an issue let me explain
Hi. I have disabled DNS service, i put in manually dns server and ip address in my network Ethernet (im on latest windows 10 x64 pro)
And i see much software on my pc tries to connect to port 53 some udp some tcp. If i block it they won't connect to the internet, BUT some software will! Like for an example, steam works fine even if i disable port 53 which it wants to connect to. Smartscreen wants to malwarebytes wants to and my brave browser.
If i disable 53 for brave browser i can't use brave it becomes offline even though i have 443 enabled for it. So as soon as i enable port 53 for it, it works again. I read this can be some kind of attack or use for someone to use for their advantage. My scans come up clean, but this is something else. It can be used to bypass firewall, i read.
"mcglvr says:
Port 53 is also used by people to bypass firewalls. Since this port may be open by default, a program like Fpipe port redirector can use it to communicate with the internet by creating a TCP stream on 53."
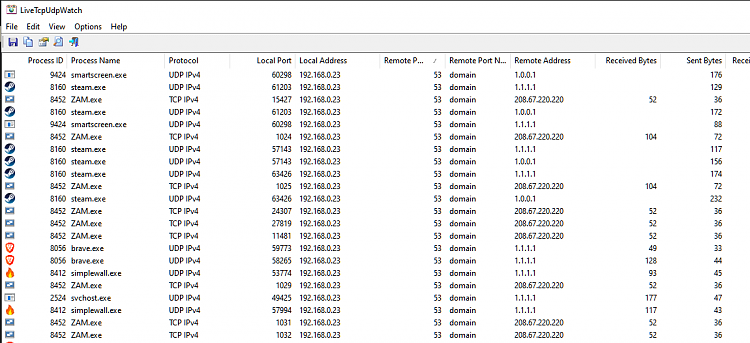
Here is some pictures taken from me



 Quote
Quote