New
#40
Windows Print Spooler Remote Code Execution Vulnerability
-
-
New #41
Denis, Thanks for checking.
Thanks for checking.
I presume this means we can keep the Print Spooler service enabled and running if we installed KB5005945 and not get hacked if
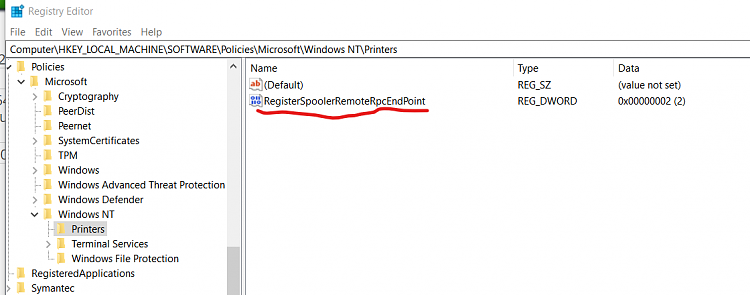
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
doesn't exit on our PC.
If I'm misinterpreting the situation, please correct me.
-
-
New #43
-
-
New #45
Do be aware anytime you print - whether printing to paper or to a document such as PDF, you're invoking (using) the Print Spooler. Bottom line is if you "print" you're using the print spooler which is the risk
BTW, if you find you can't print (and provided the printer is good) look to the print spooler service.
Anyway, I print all the time and am not about to stop now, so...
-
New #46
-
New #47
Appears that they are issuing the Adobe Flash removal tool in the same KB. It is possible that if your machine is not affected by PrintNightmare that when the Adobe removal tool runs, the patch does not apply if everything comes back that it is not a necessary OOB.
-
New #48
Microsoft has issued a statement regarding this issue: "Our investigation has shown that the OOB security update is working as designed and is effective against the known printer spooling exploits and other public reports collectively being referred to as PrintNightmare. All reports we have investigated have relied on the changing of default registry setting related to Point and Print to an insecure configuration" It appears the registry key NoWarningNoElevationOnInstall has had its value changed by some admins and that is what has caused the original fix to allegedly fail according to Microsoft. MS states that if the keys original value of 0 is left unchanged, then the patch works as intended.
-
-
Related Discussions


 Quote
Quote