Tamper protection now generally available for Microsoft Defender ATP
- Real-time protection, which is the core antimalware scanning feature of Microsoft Defender ATP next generation protection and should rarely, if ever, be disabled
- Cloud-delivered protection, which uses our cloud-based detection and prevention services to block never-before-seen malware within seconds
- IOAV (IE Downloads and Outlook Express Attachments initiated), which handles the detection of suspicious files from the Internet
- Behavior monitoring, which works with real-time protection to analyze and determine whether active processes are behaving in a suspicious or malicious way, and then blocks them
- Security intelligence updates, which Windows Defender Antivirus uses to detect the latest threats

Tamper protection now generally available for Microsoft Defender ATP
Tamper protection enabled by default for Windows 10 usersPosted: 14 Oct 2019
Attackers relentlessly up their game in bypassing security, either by using evasive techniques or, in the case of sophisticated threats like the fileless campaign Nodersok or the banking Trojan Trickbot, by attempting to disable Windows Defender Antivirus. Attackers go after real-time protection settings like OnAccessProtection policies, try to stop the Windows Defender Antivirus service, or attempt to turn off behavior monitoring and script scanning. In essence, attackers try to break the shield and take down the features that effectively work at stopping them.
One of the innovative ways in which we have hardened our solutions against these kinds of attacks is through tamper protection, a new feature designed to protect against malicious and unauthorized changes to security features, ensuring that endpoint security doesn’t go down. Earlier this year, we rolled out this feature to Windows Insiders and have been working closely with customers on developing the capability.
Today, we are excited to announce that tamper protection is now generally available!
Tamper protection prevents unwanted changes to security settings on devices. With this protection in place, customers can mitigate malware and threats that attempt to disable security protection features. Here are some examples of services and settings that are protected from modification, either by local admins or by malicious applications:
The development of this feature is a result of our extensive research into the evolving threat landscape and attack patterns, along with consistent engagement with and feedback from customers and partners. The lack of visibility of tampering attempts at various levels can make it difficult to mitigate sophisticated threats. Customer feedback on deployment and other aspects of the feature were critical in our journey towards today’s GA. Here’s what some of these customers say about tamper protection:
“Tamper protection is a critical feature for us as we need to defend Microsoft Defender ATP to ensure that malicious actions are not going around our security platforms. While complex behind the scenes, Microsoft has made it extremely easy for us to configure and deploy through Microsoft Intune and allow our SecOps team visibility into any potential tampering events so we can further investigate and remediate.” – Rich Lilly, Partner | Associate Director, Netrixllc
“Microsoft’s new tamper protection feature ensures that Lexipol endpoints remain secured and in compliance by protecting against both malicious and accidental changes to Microsoft Defender ATP’s security settings. With Microsoft Intune, managed endpoints outside of the corporate VPN can be reached with ease and the inclusion of tamper protection settings in Microsoft Intune policies has greatly simplified the deployment of this critical security feature. The combination of tamper protection and Microsoft Intune increases Lexipol’s security posture while reducing the complexity of monitoring for compliance.” – Patrick Sudderth, Director of Information Technology, Lexipol
Enabling tamper protection for enterprises through Microsoft Intune
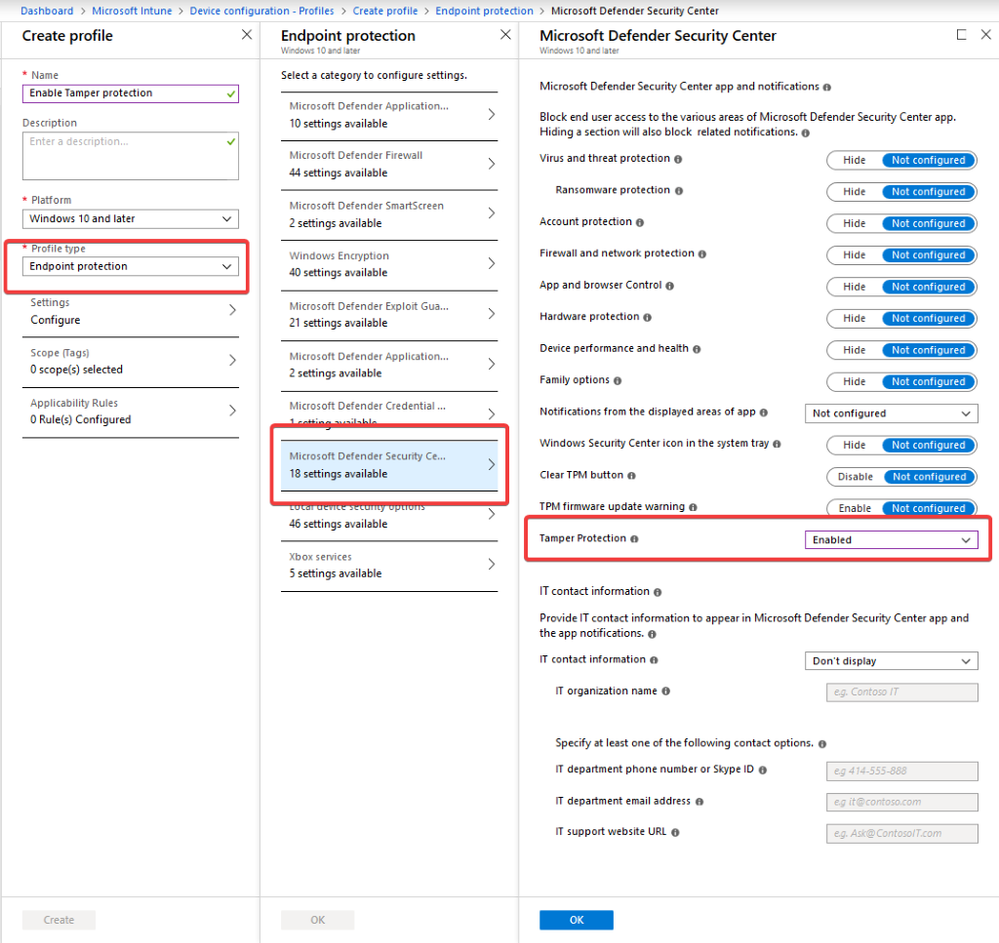
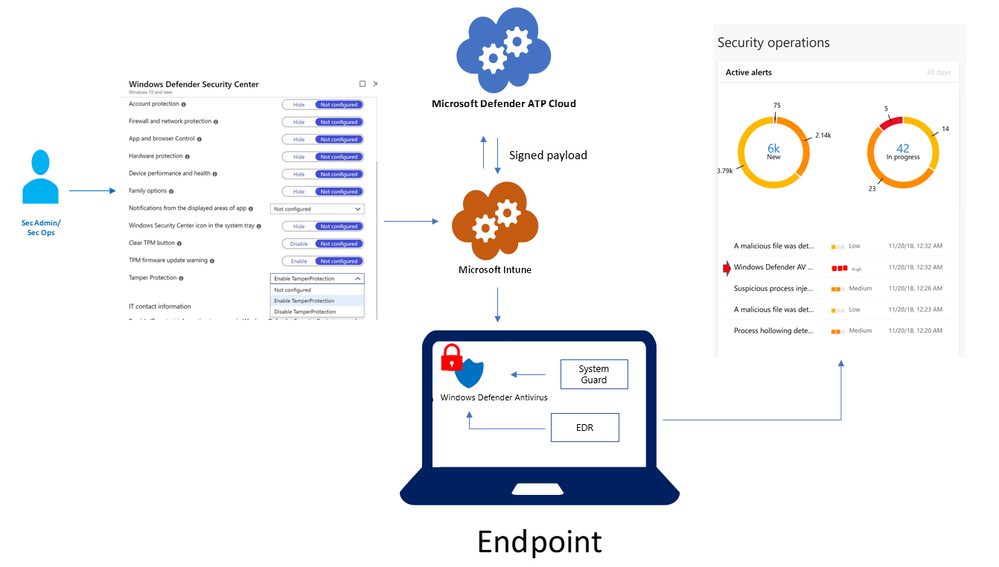
Tamper protection can be deployed and managed centrally – and securely – through Microsoft Intune, similar to how other endpoint security settings are managed. The feature can be enabled for the entire organization, or through device and user groups.
We designed deployment to be secure. We partnered with Microsoft Intune to build a secure channel to light up this feature. In this release, any changes to the tamper protection state may only be made through Microsoft Intune, not through any other methods like group policy, registry key, or WMI. Integration with other management channels will be prioritized based on customer demand.
When an administrator enables the policy in Microsoft Intune, the tamper protection policy is digitally signed in the backend before it’s sent to endpoints. The endpoint verifies the validity and intent, establishing that it is a signed package that only security operations personnel with Microsoft Intune admin rights can control. With the right level of reporting, security operations teams are empowered to detect any irregularities.
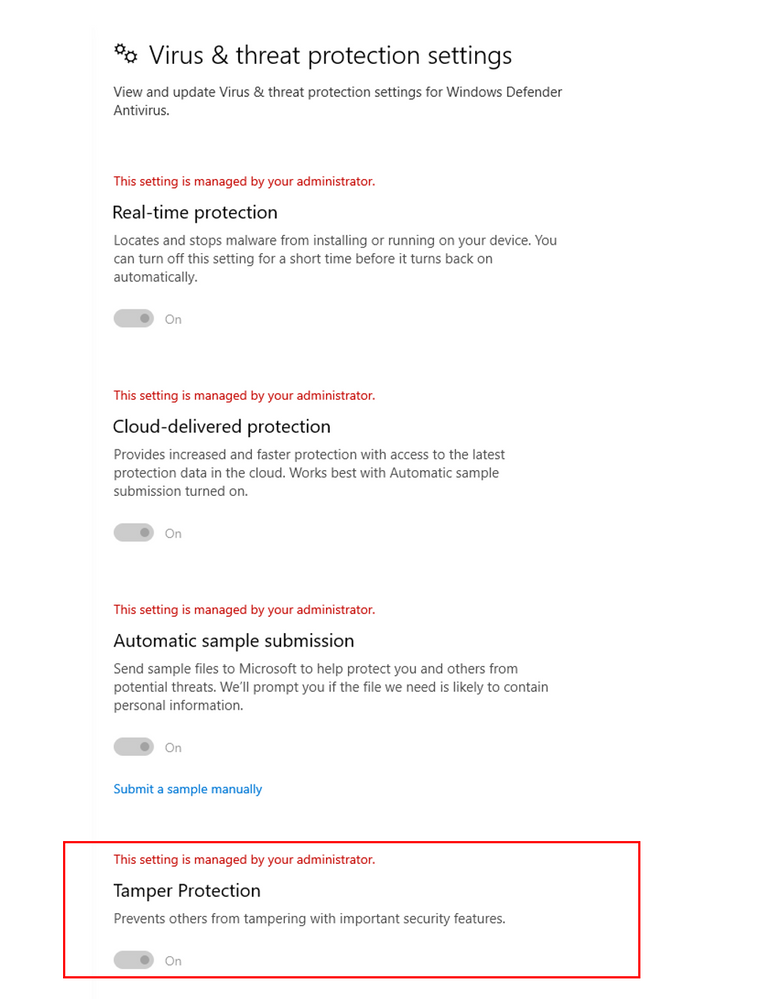
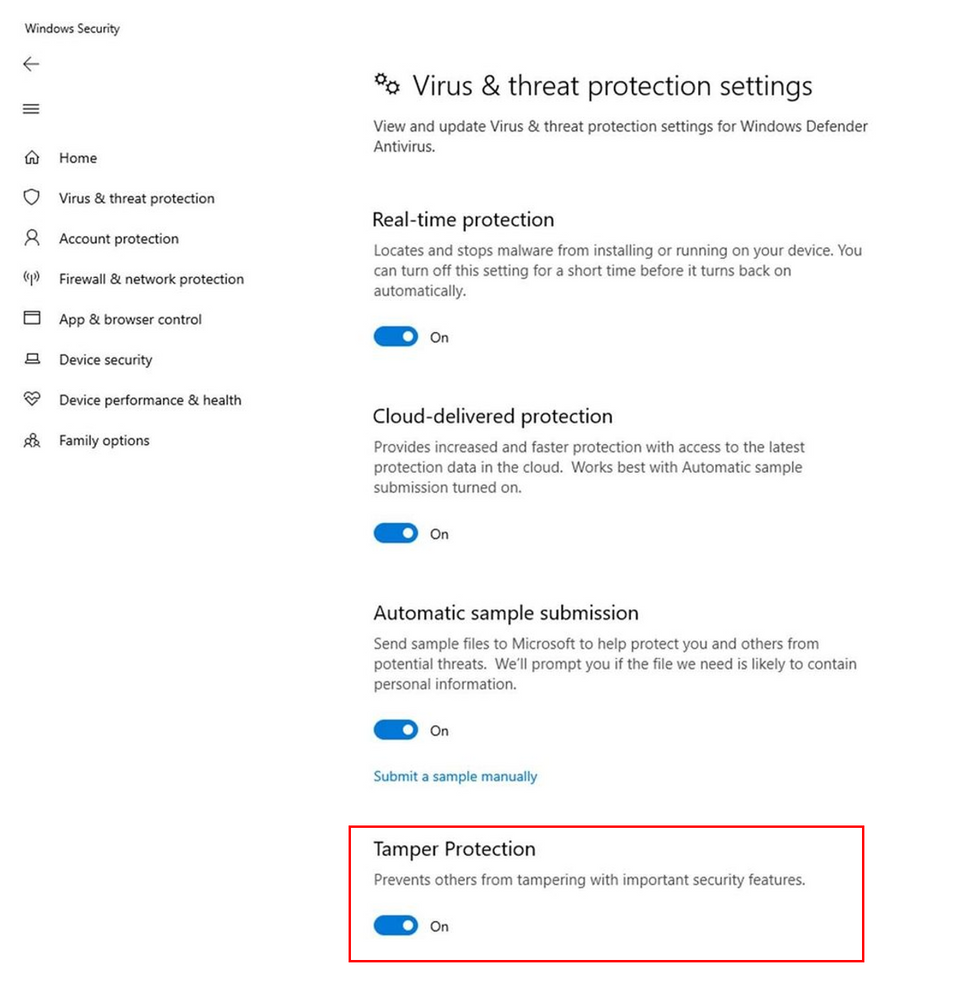
Once the feature is enabled by administrators, users will see tamper protection turned on:
To learn more, see Protect security settings with tamper protection.
Reporting and hunting for tampering attempts across organizations
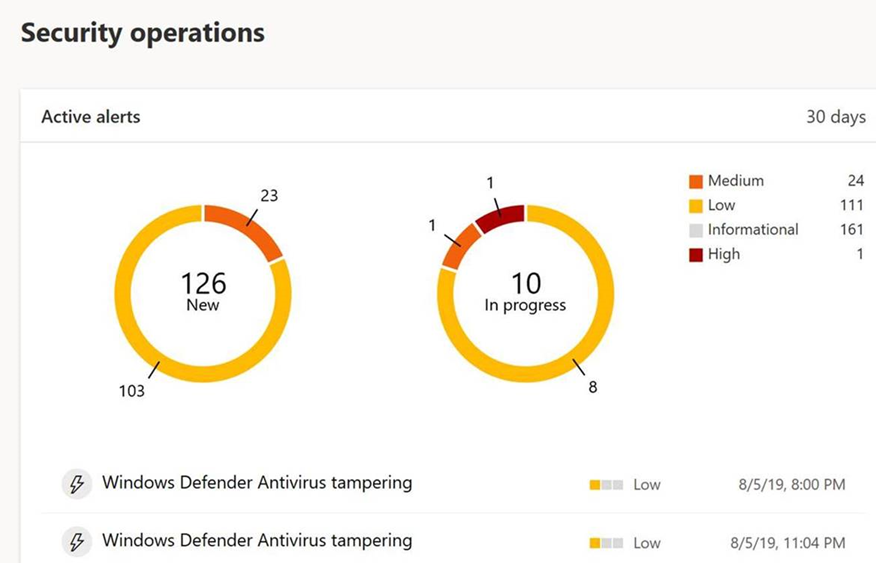
When a tampering attempt is detected on endpoints, an alert is raised in Microsoft Defender Security Center. Using the rich endpoint and detection response capabilities in Microsoft Defender ATP, security operations teams can investigate and resolve these attempts.
Tampering attempts typically indicate bigger cyberattacks where threat actors change security settings as a way to persist and stay undetected. With reporting and advanced hunting capabilities in Microsoft Defender ATP, security operations teams can hunt for tampering attacks in organizations. This empowers SecOps to detect such attacks, investigate using the rich tooling provided by Microsoft Defender ATP, and respond to and stop cyberattacks.
We’re also working on reporting device status on Threat and Vulnerability Management. This feature will be available in near future.
Tamper protection enabled by default for home users
For home users, tamper protection will be enabled by default to automatically increase defenses against attacks. We’re currently turning on the feature gradually; some customers will start seeing the setting on their devices. Customers can use the Windows Security app to review or change tamper protection settings and turn the feature on manually.
We believe it’s critical for customers, across home users and commercial customers, to turn on tamper protection to ensure that essential security solutions are not circumvented. We will continue working on this feature, including building support for older Windows versions. We’ll announce these enhancements when they become available, so watch the Microsoft Defender ATP community. In the meantime, enable tamper protection today and give us feedback.
Shweta Jha (@shwetajha_MS)
Microsoft Defender ATP team
Source: https://techcommunity.microsoft.com/...er/ba-p/911482
How to Turn On or Off Tamper Protection for Windows Defender Antivirus in Windows 10
Tweet
— Twitter API (@user) View on Twitter
Related Discussions