Windows client guidance for IT Pros to protect against speculative execution side-channel vulnerabilities
Applies to: Windows Server 2016 Version 1709, Windows Server 2012 R2 Standard, Windows Server 2012 Standard, Windows Server 2008 R2 Service Pack 1, Windows Server 2008 R2 Standard, Windows Server 2008 Service Pack 2, Windows Server 2008 Foundation, Windows Server 2008 for Itanium-Based Systems, Windows Server 2008 Enterprise without Hyper-V, Windows Server 2008 Enterprise, Windows Server 2008 Datacenter without Hyper-V, Windows Server 2008 Datacenter Servers, Windows Server Datacenter 2016, Windows Server Essentials 2016, Windows Server Standard 2016, Windows Server 2016, Windows Server 2008 R2, Windows Server 2008 R2 Datacenter, Windows Server 2008 R2 Enterprise, Windows Server 2008 R2 for Itanium-Based Systems, Windows Server 2008 R2 Foundation, Windows Server 2008 R2 Web Edition, Windows 10 version 1803, Windows 10 version 1709, Windows 10 version 1703, Windows 10 version 1607, Windows 10, Windows 7 Service Pack 1
Summary
This article will be updated as additional information becomes available. Please check back here regularly for updates and new FAQ.
Microsoft is aware of a new publicly disclosed class of vulnerabilities that are called “speculative execution side-channel attacks” and that affect many modern processors including Intel, AMD, VIA, and ARM.
Note: This issue also affects other operating systems, such as Android, Chrome, iOS, and macOS. Therefore, we advise customers to seek guidance from those vendors.
Microsoft has released several updates to help mitigate these vulnerabilities. We have also taken action to secure our cloud services. See the following sections for more details.
Microsoft has not yet received any information to indicate that these vulnerabilities were used to attack customers. Microsoft is working closely with industry partners including chip makers, hardware OEMs, and app vendors to protect customers. To get all available protections, firmware (microcode) and software updates are required. This includes microcode from device OEMs and, in some cases, updates to antivirus software.
This article addresses the following vulnerabilities:
Windows Update will also provide Internet Explorer and Edge mitigations. We will continue to improve these mitigations against this class of vulnerabilities.
To learn more about this class of vulnerabilities, see
UPDATED ON May 14, 2019: On May 14, 2019, Intel published information about a new subclass of speculative execution side-channel vulnerabilities known as Microarchitectural Data Sampling. They have been assigned the following CVEs:
Important: These issues will affect other systems such as Android, Chrome, iOS, and MacOS. We advise customers seek guidance from their respective vendors.
Microsoft has released updates to help mitigate these vulnerabilities. To get all available protections, firmware (microcode) and software updates are required. This may include microcode from device OEMs. In some cases, installing these updates will have a performance impact. We have also acted to secure our cloud services. We strongly recommend deploying these updates.
For more information about this issue, see the following Security Advisory and use scenario-based guidance to determine actions necessary to mitigate the threat:
Note: We recommend that you install all of the latest updates from Windows Update before you install any microcode updates.
UPDATED ON AUGUST 6, 2019: On August 6, 2019 Intel released details about a Windows kernel information disclosure vulnerability. This vulnerability is a variant of the Spectre Variant 1 speculative execution side channel vulnerability and has been assigned
CVE-2019-1125.
On July 9, 2019 we released security updates for the Windows operating system to help mitigate this issue. Please note that we held back documenting this mitigation publicly until the coordinated industry disclosure on Tuesday, August 6, 2019.
Customers who have Windows Update enabled and have applied the security updates released on July 9, 2019 are protected automatically. There is no further configuration necessary.
Note This vulnerability does not require a microcode update from your device manufacturer (OEM).
For more information about this vulnerability and applicable updates , see the Microsoft Security Update Guide:
CVE-2019-1125 | Windows Kernel Information Disclosure Vulnerability.
Recommended actions
Customers should take the following actions to help protect against the vulnerabilities:
- Apply all available Windows operating system updates, including the monthly Windows security updates.
- Apply the applicable firmware (microcode) update that is provided by the device manufacturer.
- Evaluate the risk to your environment based on the information that is provided on Microsoft Security Advisories: ADV180002, ADV180012, ADV190013 and information provided in this Knowledge Base article.
- Take action as required by using the advisories and registry key information that are provided in this Knowledge Base article.
Note: Surface customers will receive a microcode update through Windows update. For a list of the latest available Surface device firmware (microcode) updates, see KB
4073065.
Mitigation settings for Windows clients
Security advisories
ADV180002,
ADV180012, and
ADV190013 provide information about the risk that is posed by these vulnerabilities, and they help you identify the default state of mitigations for Windows client systems. The following table summarizes the requirement of CPU microcode and the default status of the mitigations on Windows clients.
| CVE |
Requires CPU microcode/firmware? |
Mitigation Default status |
|---|
| CVE-2017-5753 |
No |
Enabled by default (no option to disable)
Please refer to ADV180002 for additional information. |
| CVE-2017-5715 |
Yes |
Enabled by default. Users of systems based on AMD processors should see FAQ #15 and users of ARM processors should see FAQ #20 on ADV180002 for additional action and this KB article for applicable registry key settings.
Note: “Retpoline” is enabled by default if Spectre Variant 2 (CVE-2017-5715) is enabled. For more information, around “Retpoline”, follow the guidance in the Mitigating Spectre variant 2 with Retpoline on Windows blog post. |
| CVE-2017-5754 |
No |
Enabled by default
Please refer to ADV180002 for additional information. |
| CVE-2018-3639 |
Intel: Yes
AMD: No
ARM: Yes |
Intel and AMD: Disabled by default. See ADV180012 for more information and this KB article for applicable registry key settings.
ARM: Enabled by default without option to disable. |
| CVE-2018-11091 |
Intel: Yes |
Enabled by default.
See ADV190013 for more information and this KB article for applicable registry key settings. |
| CVE-2018-12126 |
Intel: Yes |
Enabled by default.
See ADV190013 for more information and this KB article for applicable registry key settings. |
| CVE-2018-12127 |
Intel: Yes |
Enabled by default.
See ADV190013 for more information and this KB article for applicable registry key settings. |
| CVE-2018-12130 |
Intel: Yes |
Enabled by default.
See ADV190013 for more information and this KB article for applicable registry key settings. |
Enabling mitigations that are off by-default may affect performance. The actual performance effect depends on multiple factors, such as the specific chipset in the device and the workloads that are running.
Registry settings
We are providing the following registry information to enable mitigations that are not enabled by default, as documented in Security Advisories
ADV180002 and
ADV180012. Additionally, we are providing registry key settings for users who want to disable the mitigations that are related to CVE-2017-5715 and CVE-2017-5754 for Windows clients.
Important: This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, see the following article in the Microsoft Knowledge Base:
Refer to KB
322756 "How to back up and restore the registry in Windows"
Manage mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown)
Important note: Retpoline is enabled by default on Windows 10, version 1809devices if Spectre, Variant 2 (
CVE-2017-5715) is enabled. Enabling Retpoline on the latest version of Windows 10 may enhance performance on devices running Windows 10, version 1809 for Spectre variant 2, particularly on older processors.
To enable default mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown)
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect.
To disable mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown)
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
A value of
3 is accurate for
FeatureSettingsOverrideMask for both the "enable" and "disable" settings. (See the "FAQ" section for more details about registry keys.)
Manage mitigation for CVE-2017-5715 (Spectre Variant 2)
To disable mitigations for CVE-2017-5715 (Spectre Variant 2):
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 1 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect.
To enable default mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown):
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
By default, user-to-kernel protection for CVE-2017-5715 is disabled for AMD and ARM CPUs. Customers must enable the mitigation to receive additional protections for CVE-2017-5715. For more information, see FAQ #15 in
ADV180002 for AMD processors and FAQ #20 in
ADV180002 for ARM processors.
Enable user-to-kernel protection on AMD and ARM processors together with other protections for CVE 2017-5715:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 64 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
To enable mitigations for CVE-2018-3639 (Speculative Store Bypass), default mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown):
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect.
Note: AMD processors are not vulnerable to CVE-2017-5754 (Meltdown). This registry key is used in systems with AMD processors to enable default mitigations for CVE-2017-5715 on AMD processors and the mitigation for CVE-2018-3639.
To disable mitigations for CVE-2018-3639 (Speculative Store Bypass) *and* mitigations for CVE-2017-5715 (Spectre Variant 2) and CVE-2017-5754 (Meltdown)
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
By default, user-to-kernel protection for CVE-2017-5715 is disabled for AMD processors. Customers must enable the mitigation to receive additional protections for CVE-2017-5715. For more information, see FAQ #15 in
ADV180002.
Enable user-to-kernel protection on AMD processors together with other protections for CVE 2017-5715 and protections for CVE-2018-3639 (Speculative Store Bypass):
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 72 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
To enable mitigations for Microarchitectural Data Sampling (CVE-2018-11091, CVE-2018-12126, CVE-2018-12127, CVE-2018-12130) along with Spectre (CVE-2017-5753 & CVE-2017-5715) and Meltdown (CVE-2017-5754) variants, including Speculative Store Bypass Disable (SSBD) (CVE-2018-3639) as well as L1 Terminal Fault (L1TF) (CVE-2018-3615, CVE-2018-3620, and CVE-2018-3646) without disabling Hyper-Threading:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 72 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
[UPDATED 5/24] If the Hyper-V feature is installed, add the following registry setting:
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f
If this is a Hyper-V host and the firmware updates have been applied: Fully shut down all Virtual Machines. This enables the firmware-related mitigation to be applied on the host before the VMs are started. Therefore, the VMs are also updated when they're restarted.
Restart the computer for the changes to take effect.
To enable mitigations for Microarchitectural Data Sampling (CVE-2018-11091, CVE-2018-12126, CVE-2018-12127, CVE-2018-12130) along with Spectre (CVE-2017-5753 & CVE-2017-5715) and Meltdown (CVE-2017-5754) variants, including Speculative Store Bypass Disable (SSBD) (CVE-2018-3639) as well as L1 Terminal Fault (L1TF) (CVE-2018-3615, CVE-2018-3620, and CVE-2018-3646) with Hyper-Threading disabled:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8264 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
[UPDATED 5/24] If the Hyper-V feature is installed, add the following registry setting:
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f
If this is a Hyper-V host and the firmware updates have been applied: Fully shut down all Virtual Machines. This enables the firmware-related mitigation to be applied on the host before the VMs are started. Therefore, the VMs are also updated when they're restarted.
Restart the computer for the changes to take effect.
To disable mitigations for Microarchitectural Data Sampling (CVE-2018-11091, CVE-2018-12126, CVE-2018-12127, CVE-2018-12130) along with Spectre (CVE-2017-5753 & CVE-2017-5715) and Meltdown (CVE-2017-5754) variants, including Speculative Store Bypass Disable (SSBD) (CVE-2018-3639) as well as L1 Terminal Fault (L1TF) (CVE-2018-3615, CVE-2018-3620, and CVE-2018-3646):
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Restart the computer for the changes to take effect. |
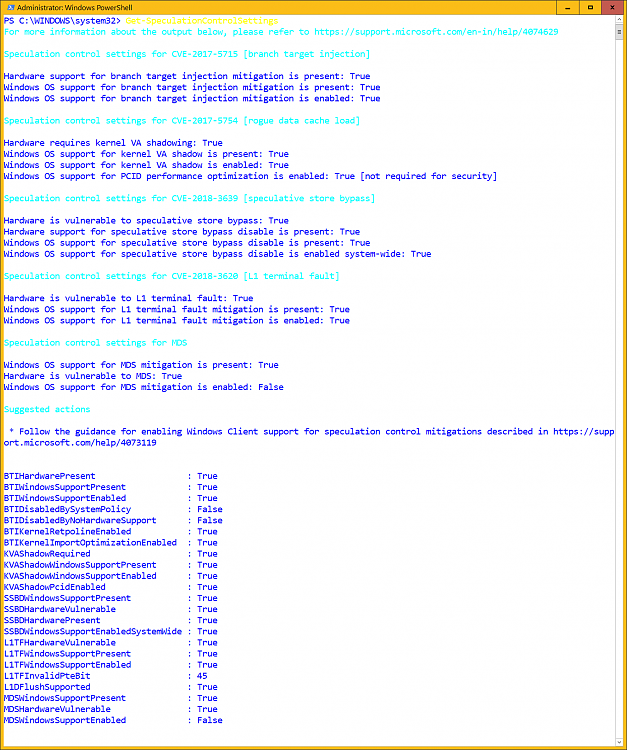
 Verifying that protections are enabled
Verifying that protections are enabled
To help customers verify that protections are enabled, Microsoft has published a PowerShell script that customers can run on their systems. Install and run the script by running the following commands.
| PowerShell verification by using the PowerShell Gallery (Windows Server 2016 or WMF 5.0/5.1) |
Install the PowerShell Module:
PS> Install-Module SpeculationControl
Run the PowerShell module to verify that protections are enabled:
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser
PS> Import-Module SpeculationControl
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser |
| PowerShell Verification by using a download from Technet (earlier operating system versions and earlier WMF versions) |
Install the PowerShell Module from Technet ScriptCenter:
Go to https://aka.ms/SpeculationControlPS
Download SpeculationControl.zip to a local folder.
Extract the contents to a local folder, for example C:\ADV180002
Run the PowerShell module to verify that protections are enabled:
Start PowerShell, then (by using the previous example) copy and run the following commands:
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser
PS> CD C:\ADV180002\SpeculationControl
PS> Import-Module .\SpeculationControl.psd1
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser |
For a detailed explanation of the output of the PowerShell script, please see
Knowledge Base article 4074629.
Frequently asked questions...

 Verifying that protections are enabled section in first post.
Verifying that protections are enabled section in first post.

Verifying that protections are enabled


 Quote
Quote
