New
#290
Yes! you have updated correctly, and you have now the latest firmwareHey, people! Did i update the ME firmware right?
Intel(R) ME code versions:
BIOS Version 1005
MEBx Version 0.0.0.0000
GbE Version 0.5
Descriptor Version 1.0
Vendor ID 8086
FW Version 12.0.35.1427 H Consumer
LMS Version 1846.12.0.1173
MEI Driver Version 1912.12.0.1247
PMC FW Version 300.2.11.1020
PCH Information
PCH Version 11
PCH Device ID A305
PCH Step Data B1
PCH SKU Type Production Pre-QS Revenue
PCH Replacement Counter 0
PCH Replacement State Disabled
PCH Unlocked State Disabled
FW Capabilities 0x31119140
Protect Audio Video Path - PRESENT/ENABLED
Intel(R) Dynamic Application Loader - PRESENT/ENABLED
Intel(R) Platform Trust Technology - PRESENT/DISABLED
Persistent RTC and Memory - PRESENT/ENABLED
Capability Licensing Service Enabled
End of Manufacturing Enable Yes
Local FWUpdate Enabled
OEM ID 00000000-0000-0000-0000-000000000000
Integrated Sensor Hub Initial Power State Disabled
Intel(R) PTT Supported Yes
Intel(R) PTT initial power-up state Disabled
OEM Tag 0x00
PAVP Supported Yes
Post Manufacturing NVAR Config Enabled Yes
TLS Disabled
FW Type Production
Last ME reset reason Global system reset
BIOS Config Lock Enabled
GbE Config Lock Enabled
Host Read Access to ME Enabled
Host Write Access to ME Disabled
Host Read Access to EC Disabled
Host Write Access to EC Disabled
SPI Flash ID 1 EF4018
SPI Flash ID 2 Not Available
BIOS boot State Post Boot
Slot 1 Board Manufacturer 0x00000000
Slot 2 System Assembler 0x00000000
Slot 3 Reserved 0x00000000
M3 Autotest Disabled
Minimum Allowed Anti Rollback SVN 1
Image Anti Rollback SVN 5
Trusted Computing Base SVN 1
Re-key needed False
HW Binding Enabled
FPF UEP ME FW
*In Use
--- --- -----
Enforcement Policy 0x00 0x00 0x00
EK Revoke State Not Revoke Not Revoke Not Revoke
PTT Enabled Enabled Enabled
OEM ID 0x00 0x00 0x00
OEM Key Manifest Present Not Present Not Present Not Present
OEM Platform ID 0x00 0x00 0x00
OEM Secure Boot Policy 0x400 0x400 0x400
CPU Debugging Enabled Enabled Enabled
BSP Initialization Enabled Enabled Enabled
Protect BIOS Environment Disabled Disabled Disabled
Measured Boot Disabled Disabled Disabled
Verified Boot Disabled Disabled Disabled
Key Manifest ID 0x00 0x00 0x00
Persistent PRTC Backup Power Enabled Enabled Enabled
RPMB Migration Done Disabled Disabled Disabled
SOC Config Lock Done Not Done Done
SPI Boot Source Enabled Enabled Enabled
TXT Supported Disabled Disabled Disabled
ACM SVN FPF 0x00
BSMM SVN FPF 0x00
KM SVN FPF 0x00
OEM Public Key Hash FPF 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash UEP 0000000000000000000000000000000000000000000000000000000000000000
OEM Public Key Hash ME FW 0000000000000000000000000000000000000000000000000000000000000000
PTT Lockout Override Counter FPF 0x00
Thanks!!!
- - - Updated - - -
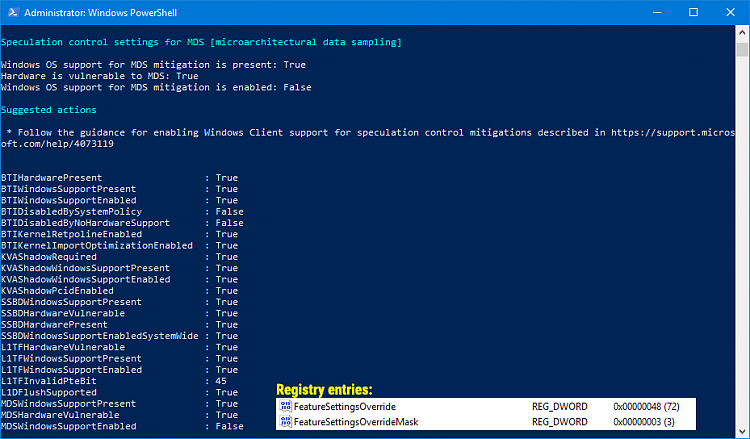
I big to differ, these values still enable other mitigations than the retpoline,
The best is to set it to 72 waiting for the microcode
- - - Updated - - -
What is your CPU?Hi JenyJ,
As I said in my post, I applied some registry tweaks. Specifically, these ones:
As far as I can tell, the only thing I accomplished was to disable hyper-threading (which protects against ZombiLoad). It did not take care of SSBD. Am I missing something?Code:reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8264 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f



 Quote
Quote