New
#430
Windows Client Guidance against speculative execution vulnerabilities
-
-
New #431
Hundreds Of Meltdown, Spectre Malware Samples Found In The Wild
by Lucian Armasu February 1, 2018 at 8:30 AM - Source: Fortinet Blo
Hundreds Of Meltdown, Spectre Malware Samples Found In The Wild
-
New #432
Thanks for the heads up @CountMike. This is not looking good
Can someone with more insight comment on this, regarding the systems that will never get new microcode for BIOS/EFI.
Few simple questions:
- malware still have to be executed, either as file or memory process, or are we at risk simply by watching video (i.e.)?
- can systems be protected with system level fixes (Windows, linux,...), if hardware is kept safe (no physical contact possible)?
-
New #433
Pretty sure that any software fix can probably be unfixed. Probably looking at a long time for any microcode fix for older processors if ever, if they can even get one that works properly.
All we can do is be more careful than usual what and where we are browsing and downloading from. The ones at risk are the ones who believe that just because they have whatever AV and anti malware, they are safe.
-
New #434
By the way, if anyone is curious and want to know their microcode revision, just run the validation in CPU-Z and it will show it here, when the validation is finished and your default browser opens:
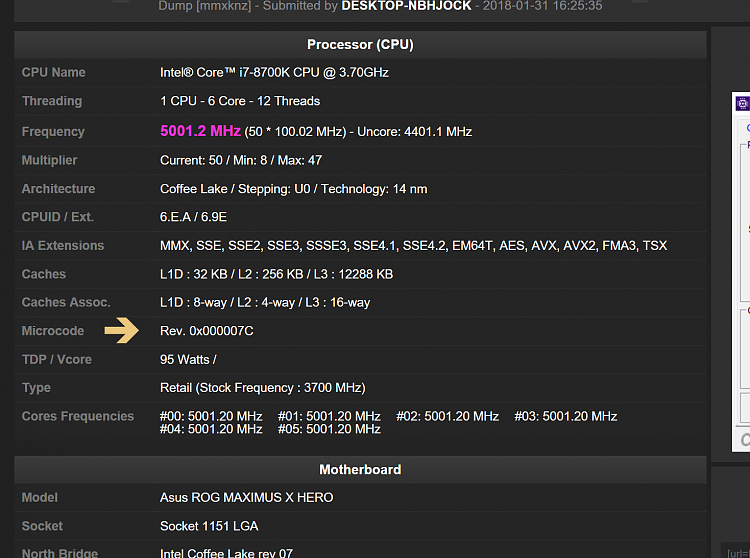
Or Aida64

And lastly, without third party software:
Open Regedit, and go to:
(Left click three times fast to select all, then copy, and paste it in Regedit's address bar)
Code:Computer\HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0
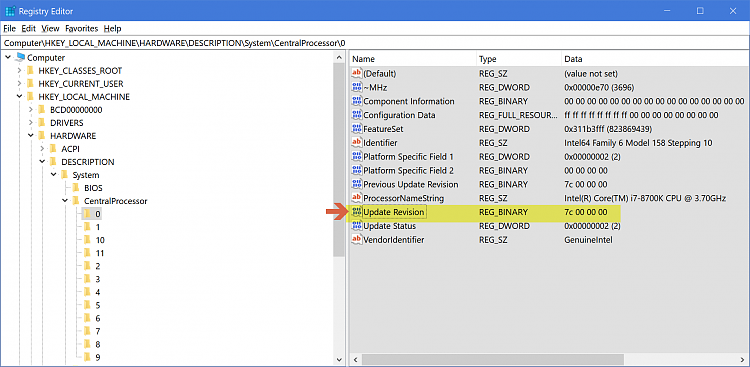
-
New #435
Aida64 is trial software.. easier to just use the best system info/monitor software out there that is also freeware HWiNFO - Download
http://www.overclock.net/photopost/d...dmicrocode.png
-
-
New #437
Thus far, it is in an executable format, and thus will need to be run on your system. Also, again, I cannot stress this enough - it is able to access privileged sections of the CPU that normally are not accessible - by dumping area.
So, it's not just a simple execute and BOOM! all your info is accessed - it has to continuously do so, because you're not always logging in to your financial accounts and such all the time.
Right now, as far as I know, it is not easily put on a local machine, and you can bet that any anti-malware worth its salt already know of the variants in the wild and are adding definitions to keep them from executing on your machine.
Finally, we have no easy way to update microcode in Windows - but it is a snap to do so in Linux, as the link I've posted to the updated microcode from Intel (which they have released many times over the years) shows the exact location to insert the code in *nix systems to make use of it.
SO, if you want to be safer, run *nix with updated microcode.
If you want to be safest disconnect from the Internet and all local networks and never introduce a new external device to your machine ever again.
And this is the only true bay to ever be safe with any machine, even those completely patched for both Meltdown and Spectre. Just by going online, even with a fully patched machine, you're taking a chance, because 0-day malware that no one has had time to research, let alone develop a signature for so your anti-malware program can block it. If you connect to a network, or connect a device from the outside that has had any sort of network (even closed ones, technically), you're automatically at risk. Period.
Powershell command to see the same:
See Supafly's post: Windows Client Guidance against speculative execution vulnerabilities - Page 42 - Windows 10 ForumsCode:reg query HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0
-
-
-
Related Discussions


 Quote
Quote
 Good one John!, Damn these non-rep-able threads
Good one John!, Damn these non-rep-able threads
 on rep!
on rep!
