Windows Client Guidance against speculative execution vulnerabilities
-
I decided to update my F.25 bios (from 2015) to F.37 which is the latest for my model as of 11/2017. Everything went fine and seems to be working well. It doesn't fix the issue since it does not contain the fix but I figure it fixes some security issues so at least it is a start. Hoping they release a new fix bios in 2/18 for my HP 15 model and I'll check back then to see if they did.
-
-
![]()
Hi,
Don't worry about it, done that hundreds of times. The main thing that can have it go south is a sudden power outage or "unthoughtful" user interference.
In almost all cases the machine can be revived by reflashing its bios/uefi or like I mentioned, recovery through jumper settings on the mainboard or whatever the OEM has come up with though.
But frankly, I've never had it go wrong. Not even in the 30 years I'm into PC's.
Cheers,

^^^^ This.
I performed my first BIOS upgrade by calling Tandy and purchasing a replacement BIOS Co for my Tandy 1000 EX 30 years ago. I have updated the BIOS on well over 100 different machines since, in various job-related and client-related positions, and have had one go bad on me only once - and that way pretty easily rectified by simply reflashing.
The key is to pay attention to what needs to be done, and best practices are to use an offline flash utility (that reboots your computer and flashes the BIOS), and then reboot again and *go directly onto the BIOS, reset, reboot, then go into BIOS again and set it up the way you head out before / the way you want to.
It is no different than any other firmware flashing technique. And no more prone to mistakes than those either.
-
Make sure your laptop is plugged into a wall outlet before doing a bios update.
Updating anything is no time to be low on power.
Jack
-
That's good. I don't think I see mine listed at all.. (HP-15 F018dx).. I....
Anyway, I'll check around 2/15 to see if anything becomes available since that seems to be the time for these other HP-15 models.
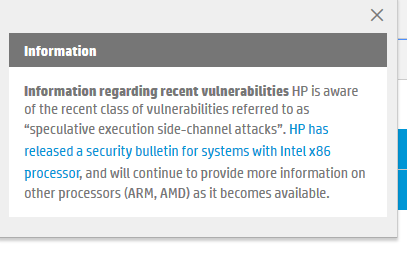
I believe my model is now listed. The new bios for it is set to be released 2/15/18 so that's good. HP is now linking to the list of bios updates from the information pop up they have had on the support site for some days now.
Separately, since I updated my bios earlier today to the latest version my computer seems faster and quieter. I like it.
-
-
The non technical can also use the file in Post #104 assuming the .Net Framework is up to date more info in posts #107 and #109
I have .Net 4.7 installed and enabled. Running the script I got a popup saying I need .Net 3.5. It gave me the option of downloading and installing 3.5 or terminating the script. From the Help provided it looks like both 3.5 and 4.7 can be enabled at the same time so I forged ahead. I'm not familiar with .Net so assumed having 4.7 enabled meant I was "up to date". Not intuitively obvious in my opinion. However, after installing 3.5 (which required a fairly lengthy download) I was able to run the script. I would say that running the script is not any more straightforward for the nontechnical than the following the instructions given earlier in the thread.
-
![]()
But now you mention it, could the cause be, the script that runs the intro when I start it, where the time and days till my next birthday(a placeholder for important Microsoft event dates), that @
Kari taught me.
For some reason I only got your mention notification now. Old post but I want to reply.
No Cliff, you are not running it elevated. When run elevated, both PowerShell and PowerShell ISE show word Administrator in Titlebar:

You might want to edit your PS script. My PS and PS ISE nowadays run this script whenever launched:
Code:
If ([bool](([System.Security.Principal.WindowsIdentity]::GetCurrent()).groups -match "S-1-5-32-544"))
{
$Mode = "elevated."
}
else
{$Mode = "in normal user mode."}
Set-Location $env:USERPROFILE
$ScriptFolder = "OneDrive\PS-Scripts"
$Scripts = $env:USERPROFILE + '\' + $ScriptFolder
Write-Host
Write-Host ' PowerShell is running'$Mode
Write-Host
Write-Host ' Scripts folder ($Scripts):'
Write-Host ' ' -NoNewline
Write-Host $Scripts
Write-Host
The script checks if I have started an elevated or a normal user mode PS and tells it to me, just to be sure:

... or:

Yes, you are running it as Admin.
No, see my reply to Cliff above.
Kari
-
Maybe people are assuming that an account with administrator authority automatically runs scripts at elevated authority. That is not the case.
-
-
Allright, so there is something weird going on on my end - I've followed all the advisories, updated CPU microcode and modified the registry to enable the branch target injection mitigation, yet it stays disabled for some reason. My Get-SpeculationControlSettings output looks as follows:

Clearly, the mitigation should be enabled as all the requirements are met, it's not disabled by ANY of the three scenarios and yet it stays disabled at all times. I am completely at a loss as to why might that be. Anyone saw something like that?
-
-
It seems you've missed some of @
Cliff S 's earlier postings and screenshots were he clearly shows how he started PS as Admin. The script brings the prompt to his user profile folder, hence the confusion.
It might be. I was referring and replying to Cliff's post here (post #32) and your reply to it in very next post (post #33).
In the post I referred to and your reply to it, Cliff's screenshot clearly shows PS is not elevated. Cliff asked if he is running elevated, the answer is no, not as shown in that post.


 Quote
Quote





