New
#50
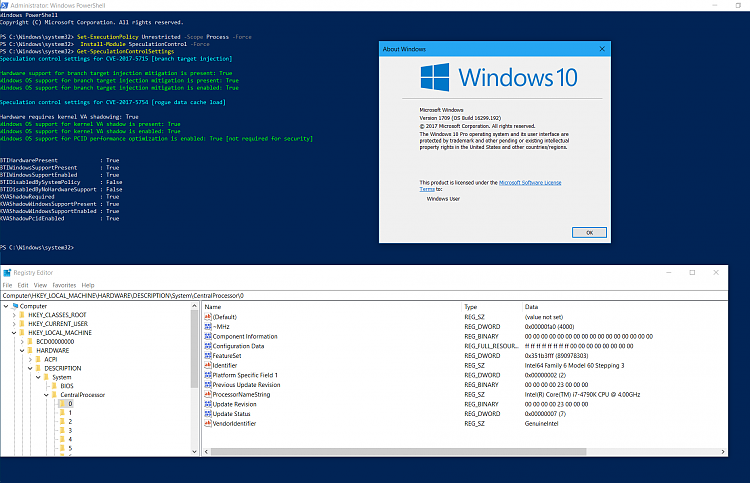
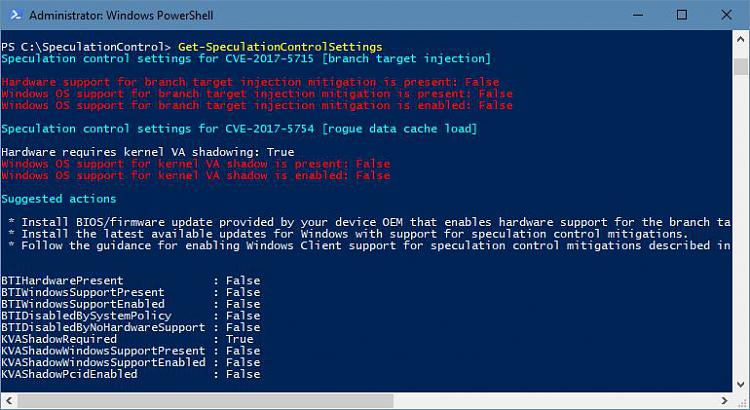
That was on my FCU partition. Below is my IP 17063 partition, which, of course, is the same BIOS, but they say we Insiders are running the latest security fixes? What a crock!
Absolutely nothing on the Asus site about this issue. Not in support or news. Zilch. I have this sinking feeling I won't be able to update this tower, nor my laptop BIOS. Probably at least half of us here will own boat anchors soon unless we get updates. If not, then these bass turd corporations will turn around and sell us more junk. Money sucking educated idiots, every one of them.
Gates had better step in on this issue to do something about it.
Attachment 171104



 Quote
Quote