How to Set Default BitLocker Encryption Method and Cipher Strength in Windows 10
You can use BitLocker Drive Encryption to help protect your files on an entire drive. BitLocker can help block hackers from accessing the system files they rely on to discover your password, or from accessing your drive by physically removing it from your PC and installing it in a different one. You can still sign in to Windows and use your files as you normally would.
New files are automatically encrypted when you add them to a drive that uses BitLocker. However, if you copy these files to another drive or a different PC, they're automatically decrypted.
BitLocker can encrypt the drive Windows is installed on (the operating system drive) as well as fixed data drives (such as internal hard drives). You can also use BitLocker To Go to help protect all files stored on a removable data drive (such as an external hard drive or USB flash drive).
Windows 10 (version 1511) introduces a new disk encryption mode (XTS-AES). This mode provides additional integrity support, but is not compatible with older versions of Windows.
You could also select to use disk encryption Compatible mode (AES-CBC) that is compatible with older versions of Windows. If you're encrypting a removable drive that you're going to use on an older version of Windows, you should use AES-CBC.
Both BitLocker Drive Encryption modes above support using 128-bit or 256-bit cipher strength.
Windows 10 uses XTS-AES 128 bit by default for operating system drives as well as fixed data drives, and uses AES-CBC 128 bit by default for removable data drives.
This tutorial will show you how to set a default encryption method (XTS-AES or AES-CBC) and cipher strength (128 bit or 256 bit) you want used by BitLocker in Windows 10.
You must be signed in as an administrator to be able to choose drive encryption method and cipher strength.
BitLocker Drive Encryption is only available in Windows 10 Pro, Windows 10 Enterprise, and Windows 10 Education editions.
The BitLocker encryption method and cipher strength you set as default is only applied when you turn on BitLocker for a drive. Any changes you make will not affect a drive already encrypted by BitLocker unless you turn off Bitlocker for the drive and turn on BitLocker for it again.
Contents
- Option One: Set Default BitLocker Drive Encryption Method and Cipher Strength in Local Group Policy Editor
- Option Two: Set Default BitLocker Drive Encryption Method and Cipher Strength in Registry Editor
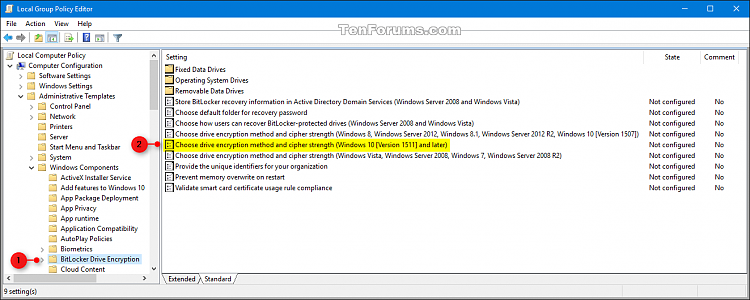
1 Open the Local Group Policy Editor.
2 In the left pane of Local Group Policy Editor, navigate to the location below. (see screenshot below)
3 In the right pane of BitLocker Drive Encryption in Local Group Policy Editor, double click/tap on the Choose drive encryption method and cipher strength (Windows 10 (Version 1511) and later) policy to edit it. (see screenshot above)
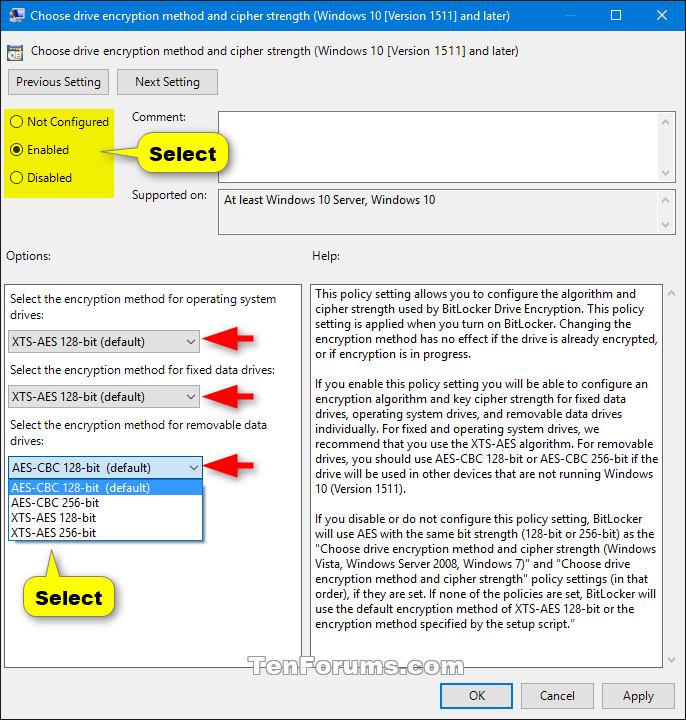
4 Do step 5 (default) or step 6 (choose) below for what you would like to do.
A) Select (dot) Not Configured or Disabled, click/tap on OK, and go to step 7 below. (see screenshot below)
Not Configured is the default setting.
A) Select (dot) Enabled, select the encryption method you want for operating system drives, fixed data drives, and removable data drives, click/tap on OK, and go to step 7 below. (see screenshot below)
7 When finished, you can close the Local Group Policy Editor if you like.
1 Press the Win + R keys to open Run, type regedit into Run, and click/tap on OK to open Registry Editor.
2 If prompted by UAC, click/tap on Yes.
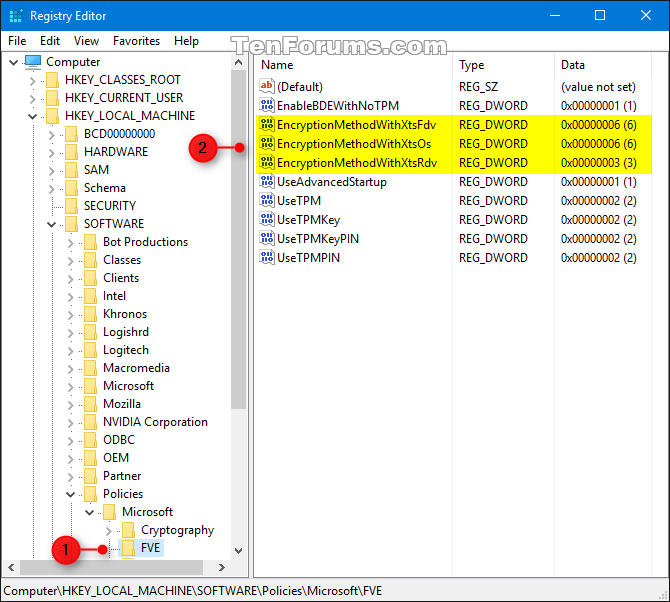
3 In Registry Editor, browse to the key location below. (see screenshot below)
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE
4 Do step 5 (choose) or step 6 (default) below for what you would like to do.
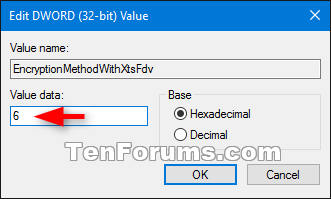
A) In the right pane of the FVE key, double click/tap on the EncryptionMethodWithXtsFdv DWORD to modify it. (see screenshot below step 3)
If you don't have the EncryptionMethodWithXtsFdv DWORD (you don't by default), then right click or press and hold on an empty area in the right pane of the FVE key, click/tap on New, click/tap on DWORD (32-bit) Value, type EncryptionMethodWithXtsFdv, and press Enter.
B) Type the value data in the table below for the encryption method and cipher strength you want for fixed data drives, and click/tap on OK. (see screenshot and table below)
Value Data Description 3 AES-CBC 128-bit 4 AES-CBC 256-bit 6 XTS-AES 128-bit (default) 7 XTS-AES 256-bit
C) In the right pane of the FVE key, double click/tap on the EncryptionMethodWithXtsOs DWORD to modify it. (see screenshot below step 3)
If you don't have the EncryptionMethodWithXtsOs DWORD (you don't by default), then right click or press and hold on an empty area in the right pane of the FVE key, click/tap on New, click/tap on DWORD (32-bit) Value, type EncryptionMethodWithXtsOs, and press Enter.
D) Type the value data in the table below for the encryption method and cipher strength you want for operating system drives, and click/tap on OK. (see screenshot and table below)
Value Data Description 3 AES-CBC 128-bit 4 AES-CBC 256-bit 6 XTS-AES 128-bit (default) 7 XTS-AES 256-bit
E) In the right pane of the FVE key, double click/tap on the EncryptionMethodWithXtsRdv DWORD to modify it. (see screenshot below step 3)
If you don't have the EncryptionMethodWithXtsRdv DWORD (you don't by default), then right click or press and hold on an empty area in the right pane of the FVE key, click/tap on New, click/tap on DWORD (32-bit) Value, type EncryptionMethodWithXtsRdv, and press Enter.
F) Type the value data in the table below for the encryption method and cipher strength you want for removable data drives, click/tap on OK, and go to step 7 below. (see screenshot and table below)
Value Data Description 3 AES-CBC 128-bit (default) 4 AES-CBC 256-bit 6 XTS-AES 128-bit 7 XTS-AES 256-bit
A) In the right pane of the FVE key, right click or press and hold on the EncryptionMethodWithXtsFdv DWORD, and click/tap on Delete. (see screenshot below step 3)
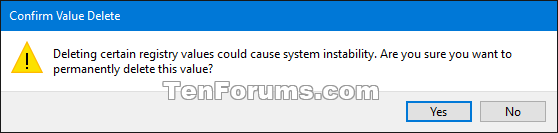
B) Click/tap on Yes to confirm. (see screenshot below)
C) In the right pane of the FVE key, right click or press and hold on the EncryptionMethodWithXtsOs DWORD, and click/tap on Delete. (see screenshot below step 3)
D) Click/tap on Yes to confirm. (see screenshot below)
E) In the right pane of the FVE key, right click or press and hold on the EncryptionMethodWithXtsRdv DWORD, and click/tap on Delete. (see screenshot below step 3)
F) Click/tap on Yes to confirm, and go to step 7 below. (see screenshot below)
7 When finished, you can close Registry Editor if you like.
That's it,
Shawn
Related Tutorials
- How to Create a BitLocker Drive Encryption Shortcut in Windows 10
- How to Turn On or Off BitLocker for Operating System Drive in Windows 10
- How to Turn On or Off BitLocker for Removable Data Drives in Windows 10
- How to Turn On or Off BitLocker for Fixed Data Drives in Windows 10
- How to Turn On or Off Device Encryption in Windows 10
Change BitLocker Encryption Method and Cipher Strength in Windows 10
-
New #1
Edit: Sorry allready there is an info box about this. I didin't saw
Hi Brink,
If apply option two directly EncryptionMethodWithXtsOs and EncryptionMethodWithXtsRdv keys doesn't exist. You have to apply option one before and then this key appears.
Therefore you have two option: Manually create keys or apply option one first.Last edited by Yasak Hayat; 14 Dec 2016 at 12:49.
-
New #2
Hello Yasak, :)
That's correct. The keys will not be there by default in OPTION TWO unless added.
-
New #3
Bitlocker and location of special folders particularly 'desktop'
Hi
Am just about to do this and need to step back. I will use the stronger cipher for all but USB drives. I will use a usb drive for authentication as well the windows password (if that's possible).
However, I have been used to using Truecrypt, partitioning all my drives to separate O/S and data. Truecrypt helpfully offered the function to mount the data drive/partition along with the system drive when the boot key was entered (as long as same key was used for both o/s and data partitions).
Now the real point of my post.....
This worked really well and allowed me to move the locations of special folders to the data drive from where I backed these up, altogether, pictures, music, videos, downloads and desktop. The latter may be an issue with Bitlocker if unlike Truecrypt, it does not offer a way of mounting data drive along with o/s at boot time - otherwise the desktop and taskbar will probably not populate properly at boot.
Need to understand this before I start encryption.
It looks like I have to encrypt the partitions separately... or can they be encrypted together i.e. whole system drive including data partition....? Happy to use the same key for both as I did with Truecrypt.
Just need to know that my desktop will load at boot from the data partition if I move the special folder to data partition.Last edited by kevvyb; 27 Jan 2017 at 14:00. Reason: typos
-
-
New #5
Thanks. Any idea on how it deals with changed location of desktop special folder at boot time? Does it mean that a password or whatever authentication is used has to be used twice, once for each partition, o/s and data partition (the latter being where I would preferably store the desktop special folder)?
-
New #6
I haven't tested to know 100%, but I would think that if you have it set to unlock the drive when you sign in to Windows 10, it'll be fine.
-
New #7
Thanks Brink. I think you are right. Have since found this:
BitLocker Auto-unlock - Turn On or Off in Windows 8
-
-
-
Posts : 5,048 Windows 10/11 Pro x64, Various Linux Builds, Networking, Storage, Cybersecurity Specialty.New #9
@Brink -
Hi. Just a major clarification...
If the drives are already set with BitLocker to XTS-AES 128-bit by default, changing this value will have no effect since BitLocker will need to be turned off and then on again (essentially redoing the whole enchilada.)
See "To Choose BitLocker Drive Encryption Method and Cipher Strength" in Step 6 of the Group Policy procedure. In Paragraph 1 of the Help it clearly states the following:
"This policy setting is applied when you turn on BitLocker. Changing the encryption method has no effect if the drive is already encrypted, or if encryption is in progress."
You can verify this by using the following command-line -> manage-bde -status which will still report the established cipher of 128, since by turning on BitLocker first the setting is "glued-in" until the BitLocker encryption setup is run again.
Only at that time will the 256-bit and other choices actually "stick" if those were the ones selected.
Can you kindly confirm?
Thanks,
Brian

Change BitLocker Encryption Method and Cipher Strength in Windows 10
How to Set Default BitLocker Encryption Method and Cipher Strength in Windows 10Published by Shawn BrinkCategory: Security System
02 Feb 2020
Tutorial Categories


Related Discussions



 Quote
Quote