New
#1
How to access Window RE without built-in Administrator account
I need help with accessing the Recovery Environment while the built -in administrator account is disabled.
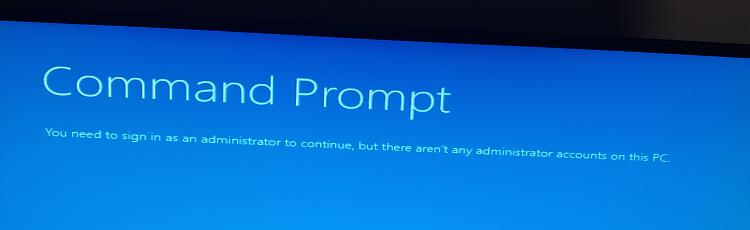
The error message that I'm getting is
"You need to sign in as an administrator to continue but there aren't any administrator accounts on this PC"
The issue might be that the only account that is active on the computer is a Microsoft account. This is the main account that I use when I use the computer. This account is in the administrators group.
Here are some thoughts and some more details on my setup:
- Is it possible to enter Windows RE with a Microsoft account?
- I believe that it should be possible to use Windows RE with an account other than the built-in administrator. The error message reads 'an administrator' no 'the (built-in) administrator' account. Does it have to be a local account?
- When I google this error, the solution seems to be to enable the built -in administrator account. I don't doubt that this would work, but I disabled that account for security reasons.
- I cannot enable/disable the built -in administrator on an as-needed basis, when I need to access Windows RE as the assumption must be that when if I need Windows RE, Windows does not boot anymore and I can't enable the built -in administrator account.
- Would I need to create an additional, local administrator account, that isn't a Microsoft account to access Windows RE?
- - - Updated - - -
Update: It is fixed.
Here is what happend:
I activated the built-in administrator and rebooted just to see if I could enter Windows RE, and suddenly two accounts were available to log in: the built-in administrator and my main account.
Then I rebooted, deactivated the built-in administrator again and booted in Win RE again and now I could login with my main account without issues!



 Quote
Quote