New
#71
New global ransomware attack hits East Europe and spreading
-
-
New #72
I'll challenge myself here to translate into laymen terms. The blue flags indicate where Microsoft's protection against the ransomware is available and mitigated the threat and eliminated it.
- A malicious software update containing the petya.dll (dynamic link library) provided by the threat actor (entity responsible for this madness) was executed upon patient zero's machine knowing it had been vulnerable, supposedly a client of a Ukrainian account company who has run into similar security issues. AppLocker would have restricted access to executable files, therefor stopping petya.
- This allows the malware to propagate and hijack the master boot record with full privileges from SeDebug.In Microsoft Windows NT, Microsoft Windows 2000, and Microsoft Windows Server 2003, you can retrieve a handle to any process in the system by enabling the SeDebugPrivilege in the calling process. The calling process can then call the OpenProcess() Win32 API to obtain a handle with PROCESS_ALL_ACCESS.More Information
This functionality is provided for system-level debugging purposes. For debugging non-system processes, it is not necessary to grant or enable this privilege.
This privilege allows the caller all access to the process, including the ability to call TerminateProcess(), CreateRemoteThread(), and other potentially dangerous Win32 APIs on the target process. https://support.microsoft.com/en-us/...debugprivilege
I just got too lazy to continue, but essentially the SMB exploits spread across the networks from available from the other machines running SMB v1 and steals network credentials, find a list of all other machines, and spreads itself again using commands from WMIC and PSEXEC for remote execution across a network and allow petya.dll to spread and hijack more MBRs.
-
-
New #74
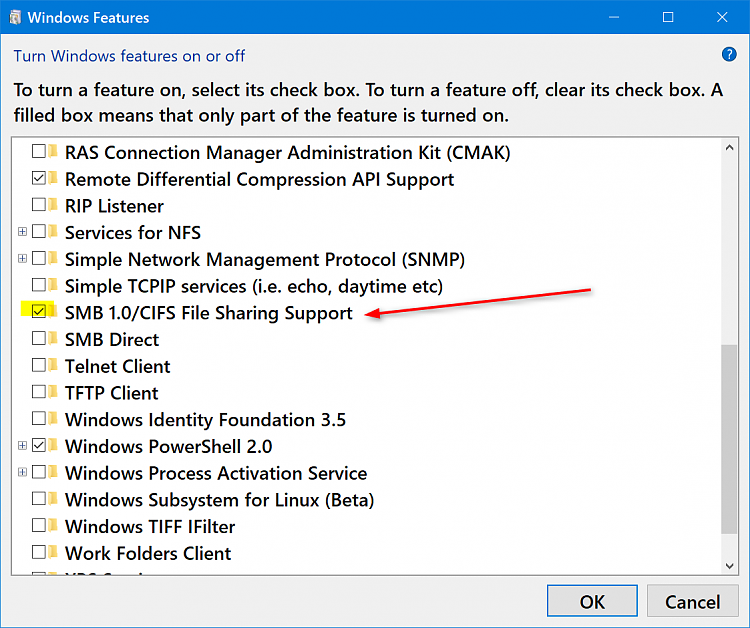
I'd think that this speaks for itself. Stop using SMB1 | Storage at Microsoft
It's not a secure protocol and the only reasons you should be running it is for Windows XP, compatibility reasons across different devices such as old printers.
So, disable it otherwise or patch your system from Petya's known attack vectors such as using WUSA for an update, MBAM, Perfmon, AppLocker, the list goes on.
-
New #75
What is the most fascinating @Wynona, malware did have strict policy to stay undisclosed. If certain AV solution was present on infected computer it went straight to destroying of file system, otherwise it went for compromising computer and checked the network for further vulnerabilities.
In my opinion, main target was collecting of credentials, or just make as much mess as they could.
-
-
New #77
Guys, don't worry so much about SMBv1 for home networks (OK, it's not something you really need), unless you have some irresponsible admin user in your network. This is not 1st line of attack. Any router will block this.
Main danger for home users is still phishing with attachments and browsing on internet.
-
-
-
New #79
-
New #80
AndreTen, I think that we can at least now state to enable Firewall protection full time on any system, whether it is running Linux, Mac OS or Windows. When troubleshooting problems, we are all going to have to remember to address the issue of if a person has a firewall enabled and make sure that everyone asks what security software they are running also. The fact that if someone blocks or disables Netbios and/or SMB ports, it will break the system.
Related Discussions



 Quote
Quote