New
#1
Default to PIN for UAC
I have two accounts in Windows 10 Enterprise:
Standard User Account (SUA) with does NOT have admin rights
Admin account which DOES have full admin rights
The admin account has a password set and a PIN set. I have UAC turned all the way up.
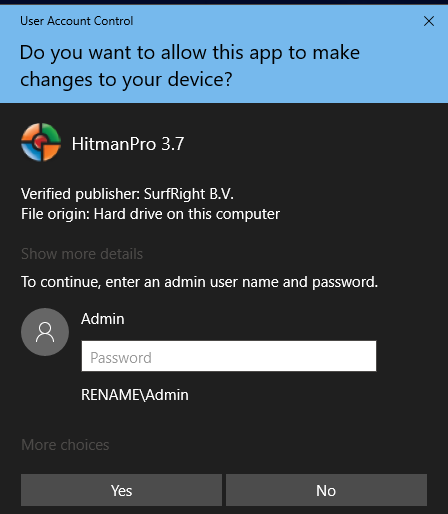
When I login with the SUA account and try to run something as ad amin I get prompted with the UAC screen as follows:
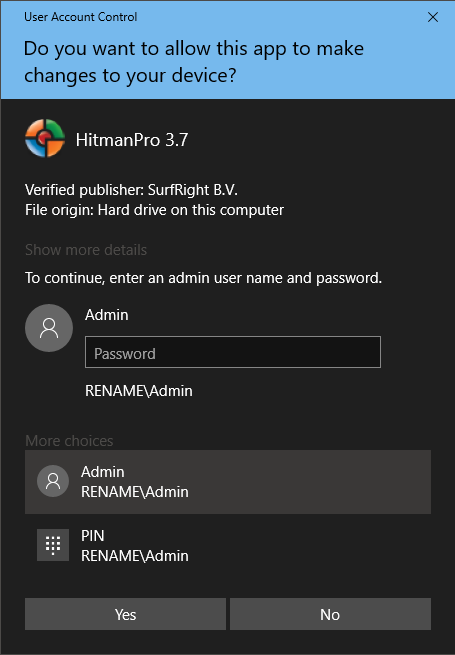
I then have to clikc "More Options" and then get prompted with the following:
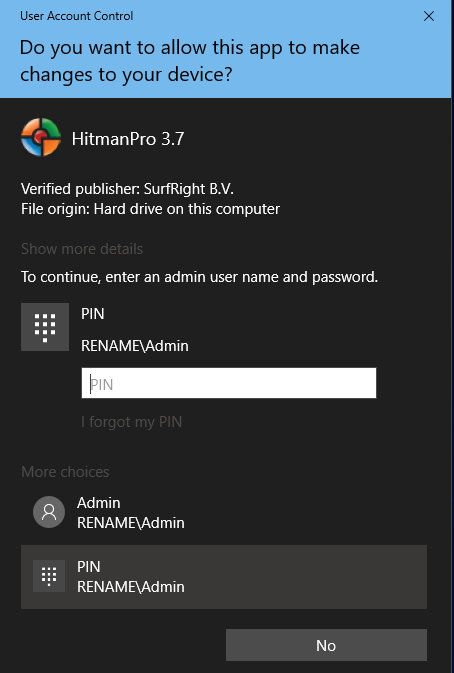
I then select PIN:
and I can enter my PIN and get the access I need for what I am doing.
The problem is that I have to select "More Options" and then PIN every single time I am prompted by UAC which is annoying.
Is there a way to force UAC to default to prompt for a PIN rather than a password?
I have researched this but all the posts talk about setting the PIN at the login screen which is not relevant to what I am trying to achieve. I am interested in setting this for the UAC prompt.
Thank you!


 Quote
Quote

