New
#81
Remove PUP application from DVD Drive (F:) CDROM
-
-
New #82
You can have a look for the log here:
The ESET Online Scanner saves a log file after running, which can be examined or sent in to ESET for further analysis. To view the log file, Show hidden files and folders must be enabled. New logs are appended to the existing log files when multiple scans are run.
The path to the log file is the following: C:\users\%userprofile%\appdata\local\temp\log.txt
-
-
New #84
I, really do want to understand the complexities of how these, or this one (for starters), infections affect systems. Could you please, tell me if this info is correct?
Poweliks is not a regular piece of malware because it resides in the memory of the system and stores absolutely no file on the disk, making it more difficult to detect.
After compromising the computer, the malware creates registry entries with commands that verify for the presence of PowerShell or .NET Framework and for executing the payload.
Once the file is launched, the cybercriminals turn on the persistency feature of the malware by creating an encoded autostart key in the registry.
It seems that the encoding technique used by the malware was originally created by Microsoft to safeguard their source code from being altered.In order to avoid detection by system tools, the registry key is hidden by providing a name in non-ASCII characters, which makes it unavailable to the Registry Editor (regedit.exe) in Windows.
By creating the auto-start key, the attackers make sure that a reboot of the system does not remove it from the computer.
By decoding the key, Symantec observed two sets of code: one that verified if the affected machine had Windows PowerShell installed, and another one, a Base64-encoded PowerShell script, for calling and executing the shellcode.
According to the Symantec researchers, the shellcode executes the payload, which attempts to connect to a remote command and control (C&C) server for receiving instructions. There are multiple IP addresses for C&C servers, all hard-coded.
The peculiarity of this malware is that it does not create any file on the disk, making it more difficult to be detected through classic protection mechanisms.
cited from: How to remove Trojan.Poweliks virus (Removal Guide)
-
New #85
Hey, how did you get tot that guide?
It means that it is sneakier than vanilla malware that can be found in a file
Let's see what the guide also idenitfied as registry keys
Command Prompt (Admin)
copy the following line and right click in the Command Prompt window to paste it
reg query "HKCU\software\classes\clsid\{ab8902b4-09ca-4bb6-b78d-a8f59079a8d5}" /s
If the query finds the key, post a screen shot.
did you perform a clean boot?
-
New #86
Yes, that is all correct.
You can also read more here:
TrendLabs Security Intelligence BlogPOWELIKS Levels Up With New Autostart Mechanism - TrendLabs Security Intelligence Blog
-
New #87
Here's a shorthand recap
Outstanding tasks:
HitmanPro - were the threats cleaned?
ESET online scan: running with auto set
Clean Boot
Reg key query
Bitdefender Rescue
TDSSKiller
Dism
SFC
Post# 1 Avast
Found a PUP
how-to-remove-driver-side-door-panel-150.ISO
The Holy Library
Holy.app
Holy.exe
8/3/2016
Post# 5 Downloads\how-to-remove-driver-side-door-panel-150.ISO
????? Avast msg says run Mnam?
Avast can not do anything, meaning "repair," "quarantine," or "delete,"?????
instead an "error" displays prompting me to run the Malwarebytes Anti-Malware scan
Post# 7: Rkill log - No objects found to stop or kill
Post# 10 ISO deleted - in recycle bin
Myrna idenfies the downloader from us1 springfile org
mixed info on research - some malicious, some 1or 2 out of all AV products flagged it
AdwCleaner log - cleaned up minor PUPs
Post# 12 JRT & HitmanPro suggested
Post# 13 - eset online suggested
Post# 15 JRT log - nothing major
Post# 24
hitman results - no threats found
Threats detected 1,095 ?????
Post# 28 suggest Mbam
Post# 32 ESET online hangs at end
Post# 35 Mbam finds Trojan.Poweliks.B in HKU\S-1-5-21
Post# 36 Mbam log two threats quarantined
Post# 37
suggest remove the two threats
suggest TDSSkiller
Post# 38 suggest How to remove the Poweliks Trojan (Removal Guide)
Post# 39 starts ReImage debacle form ad on sevenForums
Post# 49 Avast flags Poweliks guide on bleeping
Post# 50
suggest Rkill and HitmanPro from the guide
follow up with Dism & SFC
Post# 52 correction
suggest Rkill, ESET Poweliks Cleaner, and HitmanPro from the guide
Post# 60 Rkill log
Terminates 1 process
* C:\Users\MyrnaZ\AppData\Local\Temp\{7E6122F0-DB5E-430A-A6AE-6F73E75D1A32}\{BCCE466F-5194-418B-B7A4-55A77A6E62F6}.exe (PID: 16284) [T-HEUR]
This was not found in the first Rkill. Probably belongs to ReImage
Post# 63 ESET Poweliks log - threat not found
Post# 71
suggest Clean boot
Rkill
Hitman
Post# 72
suggest TDSSkiller
Bitdefender Rescue
check reg for Poweliks keys
Post# 73 Hitman log
Were they cleaned or is that just what was found?
Post# 76 suggest ESET online scanner with autoclean setLast edited by Slartybart; 18 Aug 2016 at 23:46.
-
New #88
That link to the guide is, actually a blog, although the title is the same as yours....coincidence?
How to remove Trojan.Poweliks virus (Removal Guide)
When I clicked on copy link, it had the same title. I just copied and pasted the url that is its description, above. The query did not show the key in the command prompt when I ran the line you suggested, and I will post the screen shot just so you see it:
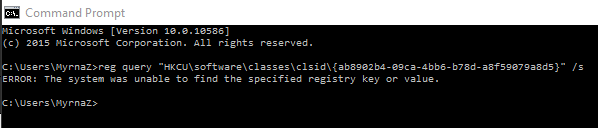
Was I supposed to reboot first? I will reboot now. Something peculiar happened when I was playing a game, yes, a game (but the one and only site I use, and please do not take my stress reliever away... ). In between rounds I noticed in the upper corner of the screen a quick "flash" of "X=x" in the same colors and font never seen previously. Am I now just being paranoid?
). In between rounds I noticed in the upper corner of the screen a quick "flash" of "X=x" in the same colors and font never seen previously. Am I now just being paranoid?
I thought I posted the results for Hitman?
-
-
-
New #90
"Son of a Poweliks mother jammer!" The recap is beyond appreciated, because trying to do things in order tends to get muddled amongst the posts written and received at different points in time. With that said, I would appreciate it if you would start using the motto:
"Do NOT be a myrnsterMash!"
Rule#
- Wait until you recieve a response before doing anything else
- Do not be a Doofus and Pay Attention to every detail
- Do NOT make the same mistake, AGAIN!
So, here is the recap, of which I began with the first item:
Outstanding tasks:
HitmanPro - were the threats cleaned?
ESET online scan: running with auto set
Clean Boot
Reg key query
Bitdefender Rescue
TDSSKiller
Dism
SFC
Tra la la, decides to go to downloads in C: Drive (no need to download the same programs, again, right), and this is what I see:
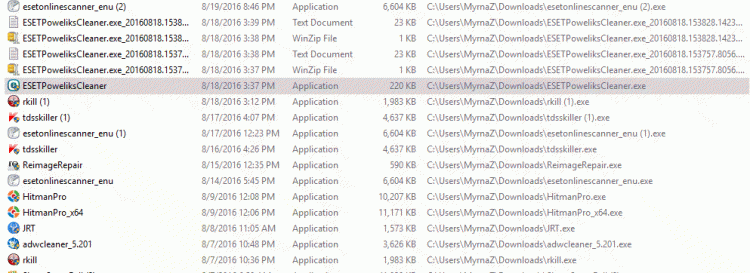
Granted, I did download the some of the same programs twice thinking it best to start "clean," but realized that was stupid, afterwards, sigh. There is not one reason, whatsoever for the .zip files, none! I have it set to ask how I want to open files, and .zip files are not supposed to open, much less run, ever. Seriously? The .zip files shown for ESET were not .zip files until I rebooted, now what?
Please, note my email in permissions...is that typical?
"Jeepers, am I being watched? I think my toaster is infected, too it keeps making crumbs, why do telemarketers know my name".....really, ugh........
What the heck.....opened the supposed log from the .zip files:
[2016.08.18 15:37:57.326] - Begin
[2016.08.18 15:37:57.328] -
[2016.08.18 15:37:57.344] - ....................................
[2016.08.18 15:37:57.346] - ..::::::::::::::::::....................
[2016.08.18 15:37:57.349] - .::EEEEEE:::SSSSSS::..EEEEEE..TTTTTTTT.. Win32/Poweliks
[2016.08.18 15:37:57.354] - .::EE::::EE:SS:::::::.EE....EE....TT...... Version: 1.0.0.5
[2016.08.18 15:37:57.357] - .::EEEEEEEE::SSSSSS::.EEEEEEEE....TT...... Built: Jun 30 2015
[2016.08.18 15:37:57.359] - .::EE:::::::::::::SS:.EE..........TT......
[2016.08.18 15:37:57.361] - .::EEEEEE:::SSSSSS::..EEEEEE.....TT..... Copyright (c) ESET, spol. s r.o.
[2016.08.18 15:37:57.368] - ..::::::::::::::::::.................... 1992-2015. All rights reserved.
[2016.08.18 15:37:57.369] - ....................................
[2016.08.18 15:37:57.369] -
[2016.08.18 15:37:57.370] - --------------------------------------------------------------------------------
[2016.08.18 15:37:57.370] -
[2016.08.18 15:37:57.372] - INFO: OS: 6.2.9200 SP0
[2016.08.18 15:37:57.372] - INFO: Product Type: Workstation
[2016.08.18 15:37:57.373] - INFO: WoW64: False
[2016.08.18 15:37:57.373] - INFO: Machine guid: DFA3F11D-1180-47E0-B36D-654F2CAE83E7
[2016.08.18 15:37:57.374] -
[2016.08.18 15:38:03.172] - INFO: Scanning for system infection...
[2016.08.18 15:38:03.174] - --------------------------------------------------------------------------------
[2016.08.18 15:38:03.174] -
[2016.08.18 15:38:03.174] - INFO: Processing [HKCU\Software\Microsoft\Windows\CurrentVersion\Run]...
[2016.08.18 15:38:03.177] - INFO: Processing [HKLM\Software\Microsoft\Windows\CurrentVersion\Run]...
[2016.08.18 15:38:03.179] - INFO: Processing [HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce]...
[2016.08.18 15:38:03.180] - INFO: Processing [HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce]...
[2016.08.18 15:38:03.181] - INFO: Processing [HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run]...
[2016.08.18 15:38:03.181] - INFO: Processing [HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run]...
[2016.08.18 15:38:03.181] - INFO: Processing classes...
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{018D5C66-4533-4307-9B53-224DE2ED1FE6}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{031E4825-7B94-4dc3-B131-E946B44C8DD5}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{1BF42E4C-4AF4-4CFD-A1A0-CF2960B8F63E}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{5999E1EE-711E-48D2-9884-851A709F543D}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{5AB7172C-9C11-405C-8DD5-AF20F3606282}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{6bb93b4e-44d8-40e2-bd97-42dbcf18a40f}]
[2016.08.18 15:38:03.182] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{71DCE5D6-4B57-496B-AC21-CD5B54EB93FD}]
[2016.08.18 15:38:03.183] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7AFDFDDB-F914-11E4-8377-6C3BE50D980C}]
[2016.08.18 15:38:03.183] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7B37E4E2-C62F-4914-9620-8FB5062718CC}]
[2016.08.18 15:38:03.183] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7D4733C0-C43B-4A81-AF43-F9B20D1F8348}]
[2016.08.18 15:38:03.183] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{82CA8DE3-01AD-4CEA-9D75-BE4C51810A9E}]
[2016.08.18 15:38:03.184] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A0396A93-DC06-4AEF-BEE9-95FFCCAEF20E}]
[2016.08.18 15:38:03.184] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A3CA1CF4-5F3E-4AC0-91B9-0D3716E1EAC3}]
[2016.08.18 15:38:03.184] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A78ED123-AB77-406B-9962-2A5D9D2F7F30}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A9DC7008-F751-405D-9DD2-BAA4CD84A705}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{AB807329-7324-431B-8B36-DBD581F56E0B}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{BBACC218-34EA-4666-9D7A-C78F2274A524}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{CB2B673F-D441-4CD4-AFBE-DC4037CA4220}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{CB3D0F55-BC2C-4C1A-85ED-23ED75B5106B}]
[2016.08.18 15:38:03.185] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{F241C880-6982-4CE5-8CF7-7085BA96DA5A}]
[2016.08.18 15:38:03.186] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{F8071786-1FD0-4A66-81A1-3CBE29274458}]
[2016.08.18 15:38:03.186] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{018D5C66-4533-4307-9B53-224DE2ED1FE6}]
[2016.08.18 15:38:03.186] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{031E4825-7B94-4dc3-B131-E946B44C8DD5}]
[2016.08.18 15:38:03.186] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{1BF42E4C-4AF4-4CFD-A1A0-CF2960B8F63E}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{5999E1EE-711E-48D2-9884-851A709F543D}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{5AB7172C-9C11-405C-8DD5-AF20F3606282}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{6bb93b4e-44d8-40e2-bd97-42dbcf18a40f}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{71DCE5D6-4B57-496B-AC21-CD5B54EB93FD}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7AFDFDDB-F914-11E4-8377-6C3BE50D980C}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7B37E4E2-C62F-4914-9620-8FB5062718CC}]
[2016.08.18 15:38:03.187] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{7D4733C0-C43B-4A81-AF43-F9B20D1F8348}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{82CA8DE3-01AD-4CEA-9D75-BE4C51810A9E}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A0396A93-DC06-4AEF-BEE9-95FFCCAEF20E}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A3CA1CF4-5F3E-4AC0-91B9-0D3716E1EAC3}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A78ED123-AB77-406B-9962-2A5D9D2F7F30}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{A9DC7008-F751-405D-9DD2-BAA4CD84A705}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{AB807329-7324-431B-8B36-DBD581F56E0B}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{BBACC218-34EA-4666-9D7A-C78F2274A524}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{CB2B673F-D441-4CD4-AFBE-DC4037CA4220}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{CB3D0F55-BC2C-4C1A-85ED-23ED75B5106B}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{F241C880-6982-4CE5-8CF7-7085BA96DA5A}]
[2016.08.18 15:38:03.188] - INFO: Processing clsid [\Registry\User\S-1-5-21-2048041476-2006749296-819459500-1005\SOFTWARE\Classes\CLSID\{F8071786-1FD0-4A66-81A1-3CBE29274458}]
[2016.08.18 15:38:03.189] - INFO: Processing [HKLM\SOFTWARE\Classes\CLSID\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32]...
[2016.08.18 15:38:03.193] - INFO: Processing value [] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.193] - INFO: Processing value [] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.193] - INFO: Processing invalid values in [HKLM\SOFTWARE\Classes\CLSID\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32]...
[2016.08.18 15:38:03.193] - INFO: Processing value [] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.194] - INFO: Processing value [ServerExecutable] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.194] - INFO: Processing value [] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.194] - INFO: Processing value [ServerExecutable] = [%systemroot%\system32\wbem\wmiprvse.exe]
[2016.08.18 15:38:03.194] - INFO: Processing invalid subkeys in [HKLM\SOFTWARE\Classes\CLSID\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32]...
[2016.08.18 15:38:03.194] - INFO: Processing [HKLM\SOFTWARE\Classes\CLSID\{AB8902B4-09CA-4bb6-B78D-A8F59079A8D5}]...
[2016.08.18 15:38:03.205] - INFO: Processing subkey [\Registry\Machine\SOFTWARE\Classes\CLSID\{AB8902B4-09CA-4bb6-B78D-A8F59079A8D5}\InprocServer32]
[2016.08.18 15:38:03.205] - INFO: Processing subkey [\Registry\Machine\SOFTWARE\Classes\CLSID\{AB8902B4-09CA-4bb6-B78D-A8F59079A8D5}\InprocServer32]
[2016.08.18 15:38:03.206] - INFO: (XSW) Scanning for XSW variant...
[2016.08.18 15:38:03.250] - INFO: (XSW) Processing users subkeys...
[2016.08.18 15:38:03.258] - INFO: Win32/Poweliks not found
[2016.08.18 15:38:13.606] - EndLast edited by myrnsterMash; 20 Aug 2016 at 16:19.
Related Discussions


 Quote
Quote