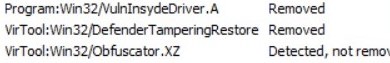New
#1
Trojan.StolenData.E !
So I have a laptop that was a victim to Trojan.StolenData.E which is a generic name to many trojans as I understood from googling , I actually discovered it manually after looking into ProgramData folder .
The program managed to decode all saved passwords in all browsers , all history from all browsers , cookies from all browsers , all searched words , all text files on laptop and zipped them into one file and I assumed to have uploaded it later to some remote location .
Luckily I do not use that laptop in any financial nor save any email passwords , mostly just forums and games .
The thing is , after using Malwarebytes , Comodo , Rogue Killer , Sophos non of these could detect what generated such file , the only detection was from Malwarebytes that detected such folder to be the work of Trojan.StolenData.E which for the casual user might seem like the threat had been detected and removed where its not , its just the work of the threat had been recognized .
So basically I know , you'd recommend resetting the laptop , but then hey now , if all these cuties up there couldn't really detect the trojan then what's the aim ? it might just come back however it did the first place .
So I have the following questions :
1- You know any better tool to detect those kinds of trojans ?
2 - Does windows offer any auditing / parenting technique to determine which process generated a file ?
3 - Why Cookies ? can cookies be used to hack an account ? like can a cookie help hijack a facebook account maybe ?
4 - Can this be the work of a script in a webpage despite that according to browsing history I haven't had any open at that time ?
-Edit-
Thought its time to update the post of search results of all main and additional anti-virus / malware suggested :
1 - Comodo : Nothing
2 - Malwarebytes : The attempt , not the cause
3 - Rogue Killer : Nothing
4 - Sophos : The search get stuck around 50% with no findings
5 - Malwarebytes Adware Cleaner : iobyte driver booster , iobyte system care , iobyte uninstaller , internet download manager , hot spot shield and avg web tuneup
6 - Hitman Pro : 47 tracking cookies (The irony)
7 - MSERT.exe by Microsoft : 3 Detection (VulnInSydeDriver.A , Defender Tampering Restore [By Comodo], Obfuscator.XZ [Detected But Not Removed])
8 - EMSISOFT : Nothing major (a random PUP PDF Lite program)
Last edited by nIGHTmAYOR; 29 Dec 2019 at 16:28.


 Quote
Quote