New
#1
Enable Retpoline to mitigate Spectre variant 2 (CVE-2017-5715)
UPDATE: 14-May-2019
Microsoft Cumulative Update KB4494441 (OS Build 17763.503), enables “Retpoline” by default if Spectre Variant 2 (CVE-2017-5715) is enabled.
In other words, Retpoline is enabled by default, in Clent SKUs with a Retpoline capable CPU, without the need to alter the Registry in any way!
Following the release of Cumulative Update KB4482887 Windows 10 v1809 Build 17763.348 there is a lot of discussion regarding the new Retpoline mitigation.
This feature has been included in the KB4482887, but is disabled by default. In future updates, or the next Feature Update (only Microsoft knows when), the feature will be enabled by default on Windows 10 clients.
So to shed some light in the issue, first we need to understand what Meltdown and Spectre, with all its variants are.
The best source of information can be found in this Microsoft article “Windows client guidance for IT Pros to protect against speculative execution side-channel vulnerabilities”
So to make a long story short, these are the most recently identified vulnerabilities, until the time this post is created:
Public Name CVE Vulnerability Exploit Name Bounds Check Bypass CVE-2017-5753 Spectre Variant 1 Branch Target Injection CVE-2017-5715 Spectre Variant 2 Kernel Virtual Address shadow /
Rogue Data Cache LoadCVE-2017-5754 Meltdown Variant 3 Rogue System Register Read CVE-2018-3640 Spectre-NG Variant 3a Speculative Store Bypass CVE-2018-3639 Spectre-NG Variant 4 L1 Terminal Fault CVE-2018-3615,
CVE-2018-3620,
CVE-2018-3646Foreshadow & Foreshadow-NG Lazy FP State Restore CVE-2018-3665 Spectre-NG Bounds Check Bypass Store CVE-2018-3693 Spectre-NG Variant 1.1 Read-only protection bypass Spectre Variant 1.2 Microarchitectural Store Buffer Data Sampling CVE-2018-12126 Fallout MSBDS Microarchitectural Load Port Data Sampling CVE-2018-12127 RIDL MLPDS Microarchitectural Fill Buffer Data Sampling CVE-2018-12130 Zombieload MFBDS Microarchitectural Data Sampling Uncacheable Memory CVE-2019-11091 RIDL MDSUM
Get the required information
- To check your PC’s status against these vulnerabilities and mitigate them, please refer to the above “Windows client guidance for IT Pros to protect against speculative execution side-channel vulnerabilities” article, install and run the referenced in the article, SpeculationControl PowerShell script.
- To check which is the recommended microcode revision for your CPU, refer to the latest intel® Microcode Revision Guidance.
- To find the CPUID (referenced in the above intel Guidance), as well as some other interesting CPU data, run the PowerShell script for CPU Information incl. CPUID and microcode revision.
Mitigate the vulnerabilities
To mitigate the vulnerabilities you must follow these simple steps:
- Check your PC’s manufacturer Support page, for an updated BIOS/UEFI. If there is one, download it and update your PC.
- If the manufacturer doesn’t provide an updated BIOS/UEFI for your PC (usually done for older PCs. It’s the manufacturer’s way of telling to buy a new one!), then look for the latest Microsoft Microcode Update for your Windows 10 version. Download it from the Windows Update catalog and apply it.
How the microcode works:
- At boot time, BIOS/UEFI loads the microcode from the firmware. This microcode comes preinstalled with your PC and is updated ONLY by a BIOS/UEFI update provided by the system manufacturer, based on code developed and made available by the CPU vendor (intel/AMD etc)
- When the OS takes over, it checks the microcode loaded by the firmware to see if it’s up to date. If it is proceeds and leaves things as they are loaded by the BIOS/UEFI. If it’s not up to date, it supersedes the BIOS/UEFI loaded microcode by the latest one, that Windows 10 have via a recent update from Microsoft. That is now becoming the “Currently Running microcode”, which is newer than the one the CPU firmware has.
- In any case this microcode is flushed upon system shutdown.
Retpoline
This is software code, developed by Google, to mitigate Spectre variant 2 (CVE-2017-5715), while providing some performance improvement by doing so, as in general the updated microcode revisions against the Spectre/Meltdown vulnerabilities tend to degrade performance.
To enable Retpoline please follow the steps in the Windows Kernel Internals blog post: Mitigating Spectre variant 2 with Retpoline on Windows
After enabling Retpoline, you will see an improvement in the performance, but don't expect anything major and certainly not performance degradation.
A couple of interesting points:
The two Registry entries, to be added or changed, as described in the above Windows Kernel Internals blog post, might exist or might not exist in your Registry.
- They might exist, if at the early stages of the Spectre/Meltdown mitigation process, you had applied a Windows update, either because your BIOS/UEFI microcode was out-of-date and the manufacturer didn’t provide an updated one, based on CPU vendor code, or worse than that, you have an old CPU, for which the CPU vendor hasn't developed new microcode.
- On the other hand, if you don’t have them, doesn’t mean that you’re not protected. It’s because either you applied a BIOS/UEFI update from your PC’s manufacturer, or you installed one of the recent (1803/1809) Microsoft provided microcode updates, which don’t create the Registry entries.
To apply the Retpoline mitigation you have to add the FeatureSettingsOverride and FeatureSettingsOverrideMask entries in your Registry (if you don’t have them) or change the two entries in the Registry (if you already have them).
- If you don’t have them just open PowerShell as Administrator and run the following two commands:
OR copy and paste the following in a text file. Save it, with an extension .reg and merge it in your Registry, by double-clicking it.Code:New-ItemProperty -Path 'Registry::\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management' -Name FeatureSettingsOverride -PropertyType DWord -Value 1024 New-ItemProperty -Path 'Registry::\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management' -Name FeatureSettingsOverrideMask -PropertyType DWord -Value 1024
Code:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management] "FeatureSettingsOverride"=dword:00000400 "FeatureSettingsOverrideMask"=dword:00000400- If you already have them, as the Windows Kernel Internals blog post says, you need to “bitwise OR” them, in other words add the hex value 400 to the one you already have.
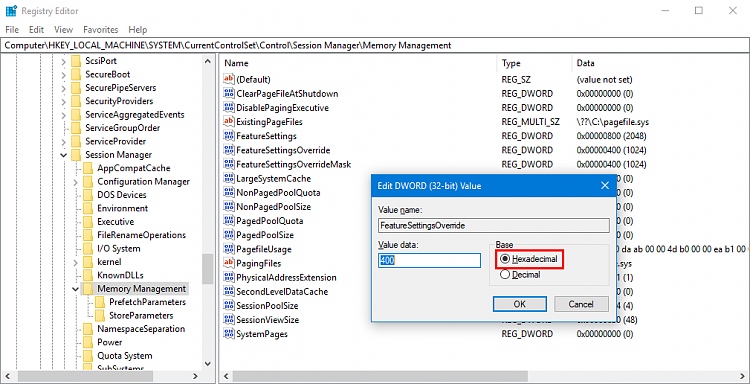
To do that find the Registry entries under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management key.
Double click on each one of them, and after making sure that you have chosen “Hexadecimal” as Base, add the hex value 400 to the one you have. For example if the value you already had was 8 type 408, if it was 3, type 403. Click OK, close the Registry Editor and reboot.
That’s it.
Not for everybody
The last thing you should have in mind is that not all CPUs are capable of the Retpoline mitigation.
According to intel, the processors based on the Intel microarchitecture codename Skylake and subsequent models will not be able to use Retpoline. In this case adding/changing the above two Registry entries will just enable the BTIKernelImportOptimizationEnabled feature and leave the BTIKernelRetpolineEnabled as false.
That’s it, so far.
Hope to have helped you.
Dimitri
Last edited by ddelo; 09 Jun 2022 at 05:44. Reason: KB4494441 Update, New MDS vulnerabilities



 Quote
Quote