Information
As most users will be aware, one restriction in Windows 10 Home is that it will not act as an RDP Server, so you cannot remote to it from another device. Additionally, you can only run 10 Home in a Hyper-V virtual machine as a basic session (as it does not have RDP server capability), and cannot then get sound.
This simple tutorial shows how to add RDP (Remote Desktop Protocol) capability to Windows 10 Home.
EDIT: Just tested for 1809 - does not seem to work. We will need an update
Here's How
Step 1: Download RDP Files in zip file format.zip
https://github.com/stascorp/rdpwrap/...rap-v1.6.2.zip
Alternatively, you can visit site below if a later version is available.
https://github.com/stascorp/rdpwrap/releases
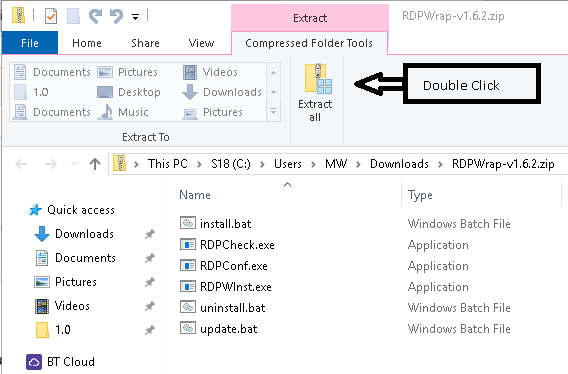
Step 2: Extract files from zip file
Double click on downloaded zip file, and select extract all.
Leave default location as is or change as you prefer and click Extract Button
Step 3: Install RDP Files
Select install.bat with a right click
and select Run As Administrator
go
The files are now installed, and you are ready to go.
Information
There is no switch to turn RDP on or off as in Pro, and so, with above steps it is always on.
To turn RDP off run UNINSTALL.BAT in same way as for running Install.Bat in this Step.
Step 4a: Connect to Windows 10 Home via RDP
This is identical to normal way of installing as described in
Add Remote Desktop Connection in Remote Desktop app on Windows 10 PC | Windows 10 Tutorials
Step 4b: Connect to Windows 10 Home in Hyper-V Enhanced Mode
This is identical to normal way of conecting to Windows PRo/Education/Enterprise in Enhanced Mode as described in
Turn On or Off Hyper-V Enhanced Session Mode in Windows 10 | Windows 10 Tutorials
That's it.
Add RDP capablity to Windows 10 Home
-
New #1
So download the bits from GitHub if you don't want to pay for Pro?
Hmmm.
-
New #2
Yep, I've been using RDPWrap on both my Win10 Home (1803) PC's for awhile now :)So download the bits from GitHub if you don't want to pay for Pro? Hmmm.
Note: When 1803 first came out I had to use the rfxvmt.dll from Win10 Pro to fix the Not Listening issue.
-
New #3
Another advantage of RDP Wrapper is that it allows multiple users to be logged in at once. I am currently on Windows 7 Home Premium with RDP Wrapper. I am signed is as a local user on the local console, and am posting this logged into the same Windows 7 Home Premium logged in as a second user via RDP. There is no indication on the local console of this second RDP connection running.
I have RDP wrapper installed on all the computers on my home network so I can log into them remotely and run backups and verify they are all getting updates without the local users (my wife or mother-in-law) being bothered by having to log off so I can log on.
The only issue is that whenever a new major upgrade of Windows comes out that changes the major version numbers of Windows, such as 1803 to 1809, you have to wait for RDP Wrapper to get updated and then update it via the local console.
-
New #4
Well it is a matter for your conscience. MS require a Pro license for RDP and a server license for multiple connection.
I'm surprised tenforums would support swapping DLL files to get features you didn't pay for.
-
New #5
Nice tut Martin
Just a small warning about RDP(not saying anyone shouldn't use it, just protect yourself):
Internet Crime Complaint Center (IC3) | Cyber Actors Increasingly Exploit The Remote Desktop Protocol to Conduct Malicious Activity
Sep 27, 2018
Alert Number
I-092718-PSA
Cyber Actors Increasingly Exploit The Remote Desktop Protocol to Conduct Malicious Activity
BACKGROUND
Remote administration tools, such as Remote Desktop Protocol (RDP), as an attack vector has been on the rise since mid-late 2016 with the rise of dark markets selling RDP Access. Malicious cyber actors have developed methods of identifying and exploiting vulnerable RDP sessions over the Internet to compromise identities, steal login credentials, and ransom other sensitive information. The Federal Bureau of Investigation (FBI) and Department of Homeland Security (DHS) recommend businesses and private citizens review and understand what remote accesses their networks allow and take steps to reduce the likelihood of compromise, which may include disabling RDP if it is not needed.DEFINITION
Remote Desktop Protocol (RDP) is a proprietary network protocol that allows an individual to control the resources and data of a computer over the Internet. This protocol provides complete control over the desktop of a remote machine by transmitting input such as mouse movements and keystrokes and sending back a graphical user interface. In order for a remote desktop connection to be established, the local and remote machines need to authenticate via a username and password. Cyber actors can infiltrate the connection between the machines and inject malware or ransomware into the remote system. Attacks using the RDP protocol do not require user input, making intrusions difficult to detect.VULNERABILITIES
- Weak passwords – passwords using dictionary words or do not include a mixture of uppercase/lowercase letters, numbers, and special characters – are vulnerable to brute-force attacks and dictionary attacks.
- Outdated versions of RDP may use flawed CredSSP, the encryption mechanism, thus enabling a potential man-in-the-middle attack.
- Allowing unrestricted access to the default RDP port (TCP 3389).
- Allowing unlimited login attempts to a user account.
EXAMPLES OF THREATS
CrySiS Ransomware: CrySIS ransomware primarily targets US businesses through open RDP ports, using both brute-force and dictionary attacks to gain unauthorized remote access. CrySiS then drops its ransomware onto the device and executes it. The threat actors demand payment in Bitcoin in exchange for a decryption key.CryptON Ransomware: CryptON ransomware utilizes brute-force attacks to gain access to RDP sessions, then allows a threat actor to manually execute malicious programs on the compromised machine. Cyber actors typically request Bitcoin in exchange for decryption directions.Samsam Ransomware: Samsam ransomware uses a wide range of exploits, including ones attacking RDP-enabled machines, to perform brute-force attacks. In July 2018, Samsam threat actors used a brute-force attack on RDP login credentials to infiltrate a healthcare company. The ransomware was able to encrypt thousands of machines before detection.Dark Web Exchange: Threat actors buy and sell stolen RDP login credentials on the Dark Web. The value of credentials is determined by the location of the compromised machine, software utilized in the session, and any additional attributes that increase the usability of the stolen resources.
SUGGESTIONS FOR PROTECTION
The use of RDP creates risk. Because RDP has the ability to remotely control a system entirely, usage should be closely regulated, monitored, and controlled. The FBI and DHS recommend implementing the following best practices to protect against RDP-based attacks:
- Audit your network for systems using RDP for remote communication. Disable the service if unneeded or install available patches. Users may need to work with their technology vendors to confirm that patches will not affect system processes.
- Verify all cloud-based virtual machine instances with a public IP do not have open RDP ports, specifically port 3389, unless there is a valid business reason to do so. Place any system with an open RDP port behind a firewall and require users to use a Virtual Private Network (VPN) to access it through the firewall.
- Enable strong passwords and account lockout policies to defend against brute-force attacks.
- Apply two-factor authentication, where possible.
- Apply system and software updates regularly.
- Maintain a good back-up strategy.
- Enable logging and ensure logging mechanisms capture RDP logins. Keep logs for a minimum of 90 days and review them regularly to detect intrusion attempts.
- When creating cloud-based virtual machines, adhere to the cloud provider's best practices for remote access.
- Ensure third parties that require RDP access are required to follow internal policies on remote access.
- Minimize network exposure for all control system devices. Where possible, critical devices should not have RDP enabled.
- Regulate and limit external to internal RDP connections. When external access to internal resources is required, use secure methods, such as VPNs, recognizing VPNs are only as secure as the connected devices.
-
-
-
New #8
Be strong with the powerless and powerless with the strong, althogh I do not care to use wrapper having myself all pro, who will rise to defend my rights to use win 10 pro without regedit being crippled in 18.03?
There is a function in regedit perfectly working in enterprise, educational that WAS working also in pro 1709, it does not work anymore, where is my right to use that function?
Anyhow I can suggest another tool "NX Nomachine" to connect win to win and also linux to win and win to linux.
@lx07 I truly apreciate your integrity, but I think ms is mistreating its userbase.
-
-
New #9

Add RDP capablity to Windows 10 Home
How to Add RDP capablity to Windows 10 HomePublished by cereberus
30 Sep 2018
Tutorial Categories


Related Discussions





 Quote
Quote